
Thales CipherTrust
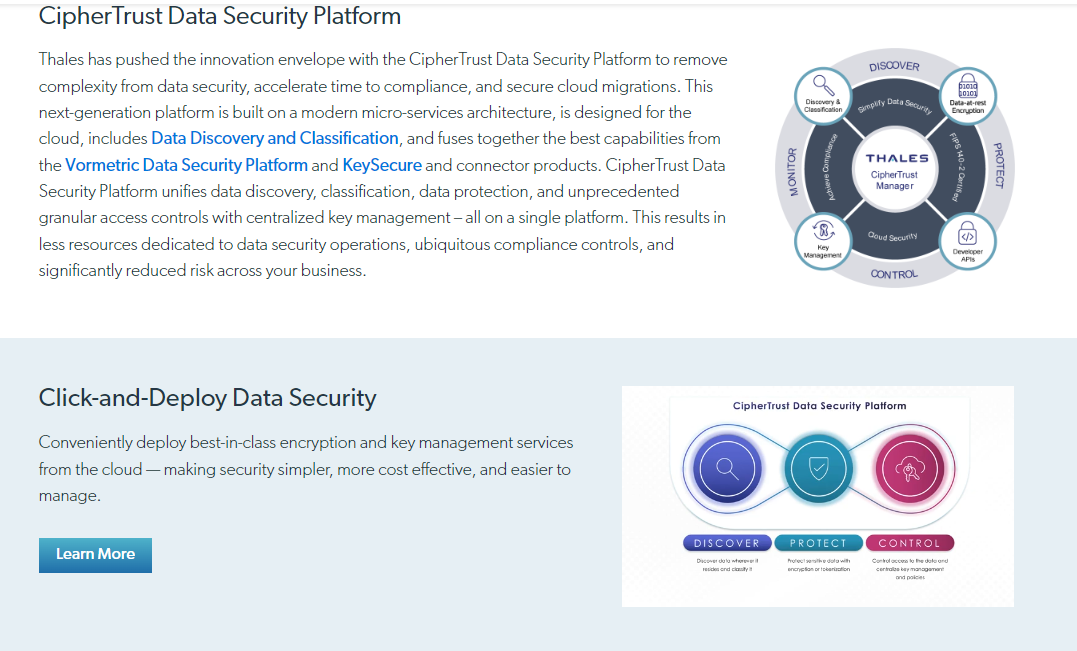
CipherTrust Data Security Platform
Specialties in Data protection, Key management, Payment security, Network encryption, Privacy regulation compliance, Cloud security, Big Data, IoT, Encryption, Cryptography, Hardware security modules, SecDevOps, data security, digital transformation, Access Management, Secure Access, HSM, and Compliance. The people you rely on to safeguard your privacy rely on Thales to protect the cloud, data, and trusted access. When it comes to data security, organisations are faced with an increasing amount of decisive moments. Whether the moment is building an encryption strategy, trusted access to the cloud, or meeting compliance mandates – you can rely on Thales to secure your digital transformation.
1893
United States
- Computer-software
- Information-technology-services
- English
Industries
-
Computer-software
-
Information-technology-services
Licensing & Deployment
-
Proprietary
-
Cloud Hosted
-
Web-based
Support
-
Email
-
Chat
-
Phone
-
24x7 Support
Knowledge Base
-
Help Guide
-
Video
-
Blog
Media
Thales CipherTrust Core Features
Focus of Network Security Feature
- Access Control
- Compliance Management
- Firewalls
- Real Time Monitoring
- Reporting & Analytics
- Threat Management
Thales CipherTrust Pricing
Pricing Type
-
Contact Vendor
Preferred Currency
-
USD ($)
Free Version
-
No
Payment Frequency
-
Quote Based
Thales CipherTrust Reviews
This profile is not claimed
Do you own or represent this business? Enter your business email to claim your Goodfirms profile.