
Trellix
Safeguard Data and Devices from Unauthorized Access
Deploy encryption policies through a single management console, while monitoring encryption status and generating compliance reports. Protect Devices Anywhere - Data on devices and removable media is protected if lost or stolen. Quickly Demonstrate Compliance
Pre-boot authentication options for multi-user environments and device status reports. Save Time and Resources. Administer policies from a single console and offer user self-service options.
Pre-boot authentication options for multi-user environments and device status reports. Save Time and Resources. Administer policies from a single console and offer user self-service options.
2022
United States
- Computer-network-security
- Computer-software
- Information-technology-services
- English
Industries
-
Computer-network-security
-
Computer-software
-
Information-technology-services
Licensing & Deployment
-
Proprietary
-
Cloud Hosted
-
On Premises
-
Web-based
-
Windows
-
Mac
Support
-
Email
-
Chat
-
24x7 Support
Training
-
Webinar
Knowledge Base
-
Help Guide
-
Video
-
Blog
Media
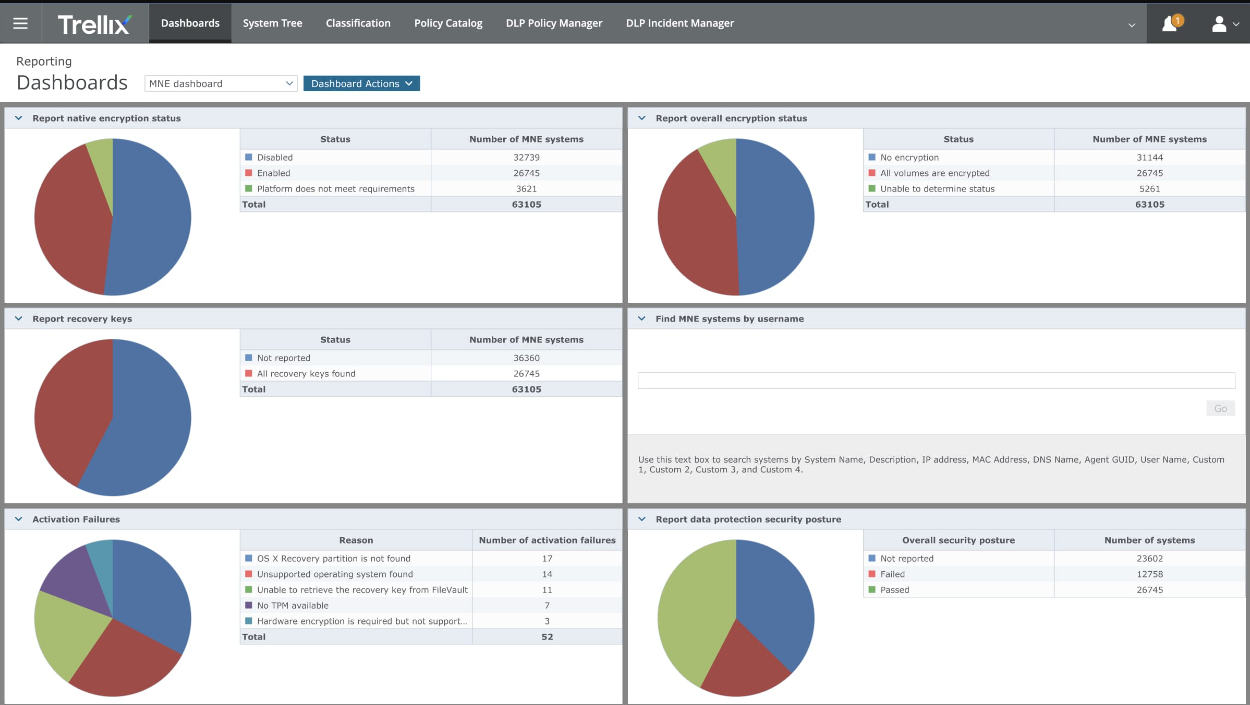
Trellix Core Features
Focus of Encryption Feature
- Strong Encryption Algorithms
- File and Disk Encryption
- Secure Key Management
- User Authentication and Access Control
- Encryption of Data in Transit
- Transparent Encryption
- Data Integrity & Authenticity Checks
- Cross-Platform Compatibility
- Secure Backup & Restore
- Integration with Existing Systems
- Compliance with Regulations
- Zero-Knowledge Architecture
Trellix Pricing
Pricing Type
-
Contact Vendor
Preferred Currency
-
USD ($)
Free Version
-
No
Payment Frequency
-
Quote Based
Trellix Reviews
This profile is not claimed
Do you own or represent this business? Enter your business email to claim your Goodfirms profile.