Work from home has become a norm due to the Covid-19 pandemic. While there are many advantages, WFH has also brought a host of new issues for companies. Cyber breaches are one of them.
Diligent took a survey of 450 professionals in UK-listed businesses. The results show that businesses lost £374 million in 2021, mainly due to cyber breaches caused by employees working from home.
Here are some stats regarding work from home security breaches:
- 64% of companies reported that they had experienced a cyberattack in the past 18 months
- 82% of those resulted from tech issues or behavior related to working from home
- 75% say their organization lost revenue – a total of £374 million – due to a breach
Most companies rely on VPNs for security, but are they foolproof? On October 12, 2020, a new vulnerability was discovered that affected nearly 800,000 internet-connected devices using the SonicWall VPN. The vulnerability was caused by a security bug in the SonicWall VPN portal, which could have caused the device to crash and allowed easy remote code execution.
The point is: VPN bugs are dangerous for many reasons. These systems expose entry points into sensitive networks, and it is difficult for system admins to recognize when a breach has occurred. Attackers can breach a VPN and then spend months mapping out a target network before deploying ransomware or making extortion demands.
It was also found in September 2020 that the default configuration for FortiGate VPNs allows for Man-in-the-Middle (MitM) attacks.
The NSA released an advisory that VPNs are vulnerable to attacks if they are not appropriately configured. Here is what they said:
.jpg)
Even if the Covid-19 suddenly vanishes from the earth, remote working isn't going anywhere now. It is here to stay. What companies have to do is adopt a better security model and also ditch their VPNs. In this blog, I will share a better alternative for cyber security. Continue reading to find it out.
Critical Cisco Bugs Leave VPN Routers Vulnerable To Cyberattacks
As of writing this blog, it was discovered that there are critical security vulnerabilities in Cisco's small business RV series routers.
The RV series is a set of VPN appliances that enable remote employees to connect to a company network. They have built-in firewalls, advanced encryption, and authentication features.
These vulnerabilities could allow privilege escalation and remote code execution with root privileges on devices.
As per Cisco's Wednesday advisory, attackers could exploit the bugs and do the following:
- Execute arbitrary code
- Elevate privileges
- Execute arbitrary commands
- Bypass authentication and authorization protections
- Fetch and run unsigned software
- Cause denial of service (DOS)
My purpose behind sharing this incident is to show you the flaws of using VPNs and how immense damage it can cause to your company.
So, it's high time to ditch your VPNs. But is there a better alternative to it? Yes!
Zero Trust Security Network: A Better Alternative For Cyber Security
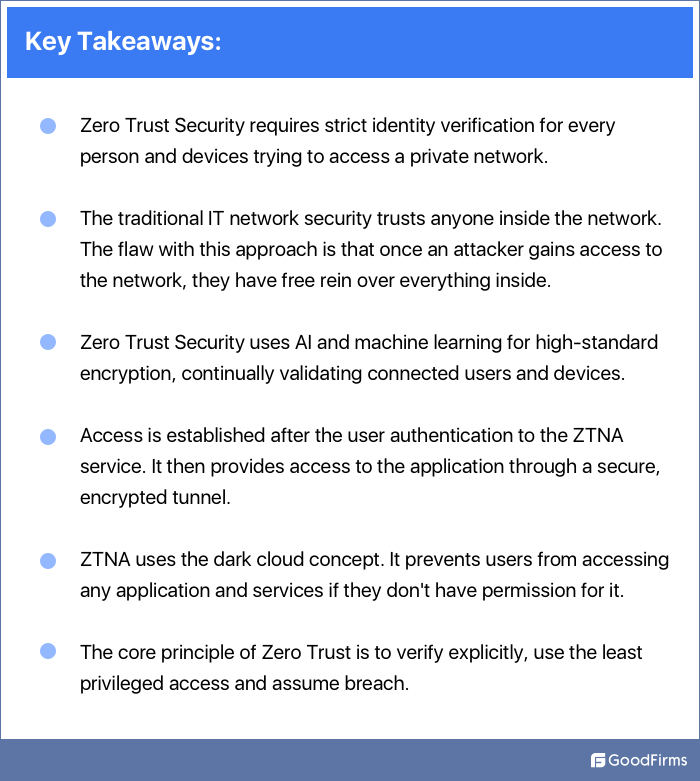
Zero Trust Security requires strict identity verification for every person and device trying to access a private network. Whether you are working in-office or at home, ZITNA covers both.
The traditional IT network security trusts anyone inside the network. It is based on the castle-and-moat concept. Here, obtaining access from outside the network is hard, but everyone inside is trusted by default. The flaw with this approach is that once an attacker gains access to the network, they have free rein over everything inside.
A Zero Trust Security trusts no one. It uses artificial intelligence and machine learning to validate connected users and devices continually like high-standard encryption.
How Does Zero Trust Network Access Work?
Access is given after the user has been authenticated to the ZTNA service. The service then provides access to the application through a secure, encrypted tunnel, which provides a layer of protection for applications and services by shielding publicly visible IP addresses.

(Source: Microsoft)
ZTNA uses the concept of a dark cloud. It prevents users from accessing any application and services if they don't have permission. So, even if there is a breach, the other services will not be affected as the attacker won't be able to access them.
- Access Control
ZTNA services have identity-based authentication and access control. It allows companies to implement location or device-specific access control policies, to prevent vulnerable devices from connecting to a company's services.
ZTNA resolves the challenges that occur with using VPN, where remote users are granted the same level of access as the ones from the company office, ignoring the possibility that they may have fewer security measures in place.
- Visibility and Control With SASE
ZTNA does not allow inspection of user traffic from the application after the person establishes the connection. It prevents security issues when a user's device or credentials gets compromised or when a malicious insider tries to disrupt the application or host.
Secure access service edge (SASE) solutions can incorporate ZTNA identity-based authentication and access control capabilities to provide a holistic approach. SASE provides the cloud scalability, security, and network capabilities for secure remote access.
They also provide post-connect monitoring for signs of compromised credentials or data loss.
SASE solution with ZTNA, can provide both protection and access control for your company.
But, what about mobile apps? Are they safe? No!
Mobile App Risks Have Increased Manifold!
Here are some examples of security weaknesses that were found from popular mobile apps:
- Mobile vulnerabilities in the Apple native email app allowed attackers to access and manipulate emails and the device itself.
- Business apps like Slack had a bug that leaked passwords.
- Mobile file sharing apps like SHAREit's security bug had remained unpatched for more than three months.
- Mobile call recording apps like Call Recorder had a bug that exposed thousands of call recordings.
- Four critical-severity flaws were disclosed in Samsung Galaxy smartphones' Find My Mobile feature. It could have allowed attackers to force a factory reset on the phones or spy on users.
- Transit Apps With 600,000 Downloads Compromised to target military and political data
Now, all of these examples are old news, and the issues have been resolved. But, my point stands that mobile app development companies need to have better security standards. But, corporate companies should not wait for them to do it. They should take security into their own hands by implementing Zero Trust Network.
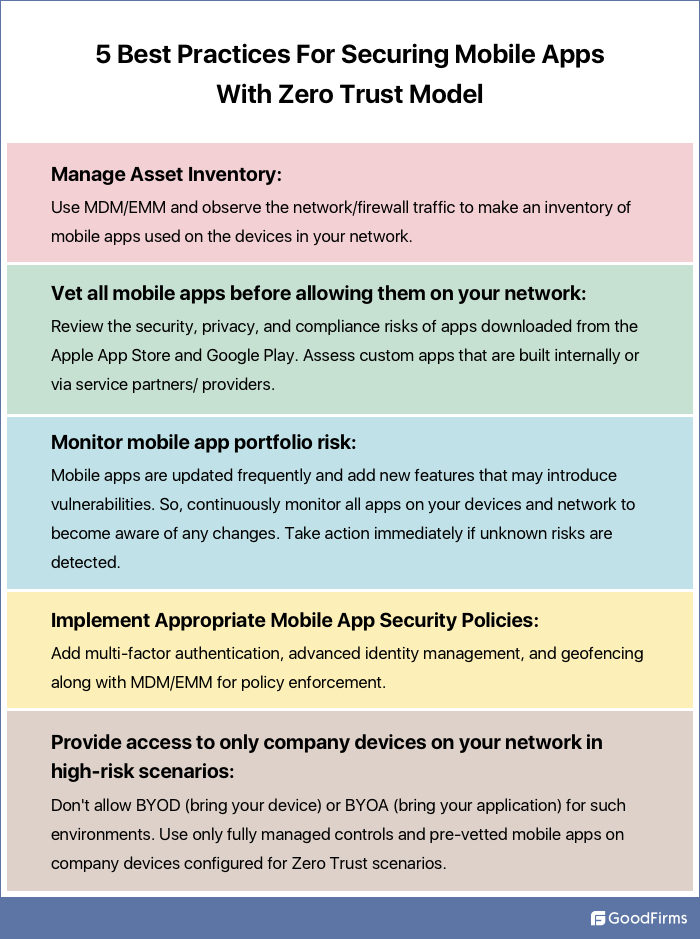
Essential Components that Businesses Should Take Into Account When Implementing ZTNA

The core principle of Zero Trust is to verify user identity and privileges explicitly, in addition to device identity and security, grant least privilege access as opposed to privileged access and assume breach. The essential question now is, how to implement it?
How Can Companies Implement Zero Trust Security To Address Cybersecurity Challenges?
Here is a five-step model for implementing and maintaining Zero Trust for Cybersecurity:
- Define the protected surface: A protected surface focuses on defending what matters to the company instead of covering the entire attack surface or focusing on just the perimeter. The protected surface is much smaller than the attack surface or the perimeter, making it easier to defend.
Reducing the attack surface is not a sound strategy due to the evolving threat landscape. The attack surface is continually expanding. With Zero Trust, instead of focusing on the attack surface, you decide your protected surface. The protected surface includes critical data, applications, assets, and services.
- Check the transaction flows: The way traffic moves across a network shows how to protect it. So, it's essential to have an insight into the interdependencies of your DAAS (Data, Applications, Assets, Services). Document how each resource interacts with the other. It will allow you to enforce controls to protect your data.
- Create An Architect of a Zero Trust Network: Zero Trust networks are customizable. It can be constructed around the protected surface. Once you have defined the protected surface and mapped the transaction flows, you can establish the Zero Trust architecture.
- Establish a Zero Trust Policy: Once the network is created, it's time to make Zero Trust policies using the "Kipling Method" to safelist which resources should have access to others. With this method, you can define the following:
- Who should be given the permission to access the resources?
- Which application is being used in accessing the resources inside the protected surface?
- At what time are the resources being accessed?
- Where is the destination of the packet?
- Why is this packet trying to gain access to this resource?
- How is the packet accessing the protected surface?
With this policy enforcement, only known allowed traffic or legitimate app communication is permitted.
5. Monitor the network: The final step involves reviewing every log, internal and external, all the way through layer 7, focusing on operational aspects of Zero Trust. Inspecting and logging all traffic will provide insights into improving the network over time as Zero Trust is an iterative process.
After completing the five-step methodology for implementing a Zero Trust network, move other data, applications, assets from your old network to a Zero Trust network in a cost-effective and non-disruptive way.
4 Zero Trust Use Cases
Here are four use cases regarding Zero Trust:
- Privileged Access Management (PAM)
Pam provides controlled access to specific devices. It ensures no passwords are unknown and enforces extra security measures like recording for supervision, full auditing, and biometric authentication.
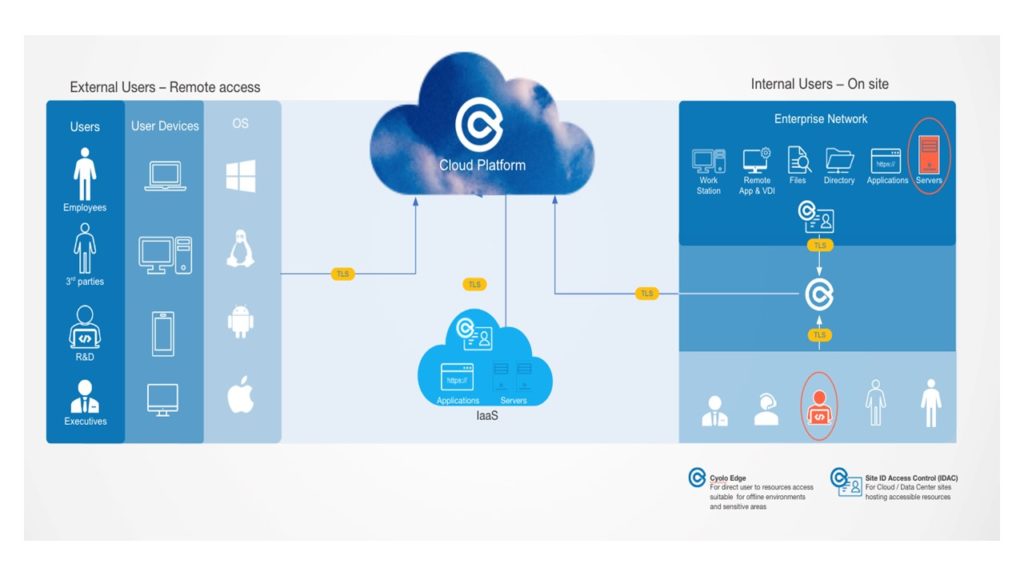 (Source: Cyolo)
(Source: Cyolo)
For example, a system admin wants to access some servers through a private network. For a secure zero trust journey, ensure:
- Limited access
- Access policy enforcement
- Logging all actions
- Auditing possibilities
For sensitive assets:
- Grant and control the access in real-time
- Have real-time visibility into the admin's action during the session
- Suppliers and 3rd Party Access
Suppliers, partners, and third parties are part of the organization's ecosystem and need connectivity for collaboration. So, provide secured and controlled external access to users with unknown devices for accessing company assets.
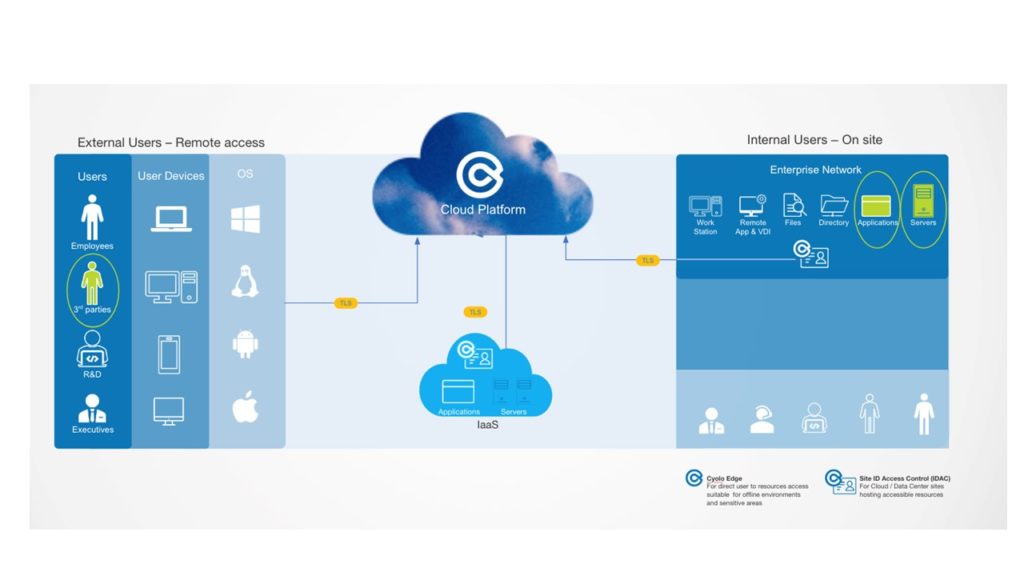
(Source: Cyolo)
For example, a supplier needs to access the company ERP (enterprise resource planning) and one of the servers.
It is recommended to:
- Require explicit real-time approval
- Grant real-time limited access
- Provide specific, limited rights like limiting copy/paste or file transfer rights to reduce the danger of data leaks and malware outbreaks.
With these security measures, you won't need to connect the supplier through a VPN or the company's managed devices. The business collaboration will now be secure and easy.
- Operational Technology (OT)
OT requires secure access for company clients while restricting network access and running production lines.
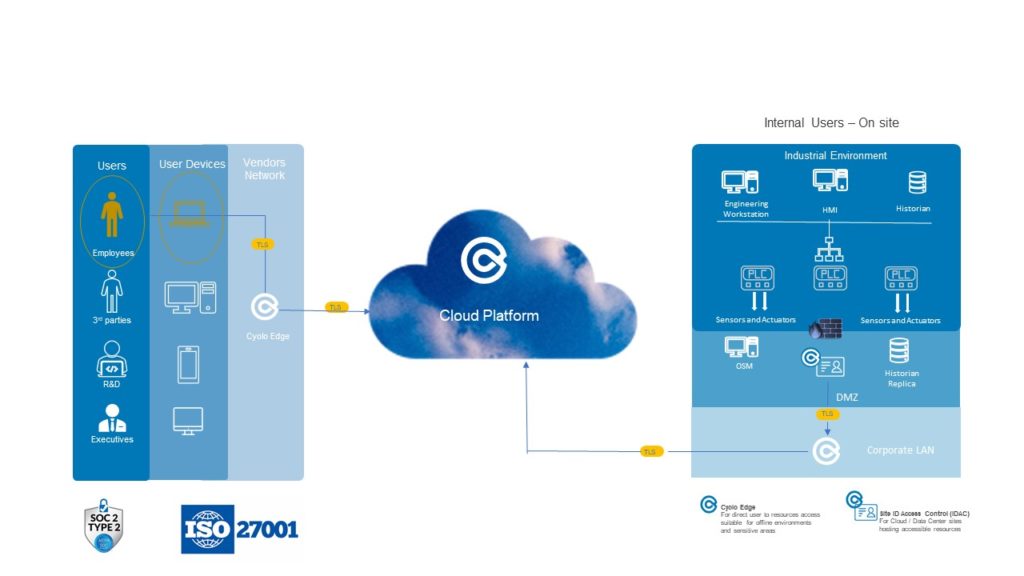
(Source: Cyolo)
For smooth operation of production lines, ensure:
- Network access through an ICS subnet
- Biometric authentication instead of passwords
- Activity recording in the network for supervision
- Monitoring access control in the network. Both for online and offline environments
- Working from Home
Companies need to securely connect remote employees to their applications, servers, desktops, and files.
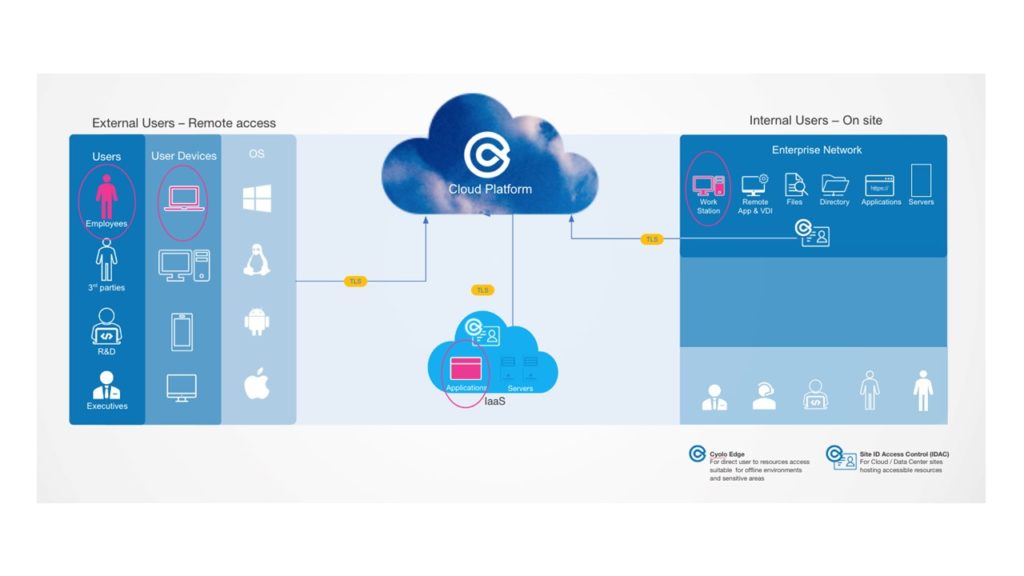
(Source: Cyolo)
For example, a WFH employee uses their laptop to access the company CRM and office desktop.
For smooth and secure connection:
- Verify the ID before access
- Encrypt the traffic
- Enforce MFA
- Monitor activities in real-time for detecting suspicious behavior
- Make it compulsory to get real-time approval from someone trusted within the company
GoodFirm's Opinion: Your company's security is in your hands. Not the VPNs you use, not the mobile app development companies whose apps your employees use in your devices. The prospects of cyberattacks should not be taken lightly. So, don't waste more time implementing Zero Trust Security if you haven't already, as it's the future.