In this digital era, if you are running a business, it is essential to understand the significance of data encryption - an invisible shield to protect sensitive data and information securely. With the rise of cyber threats and data privacy it has become critical for organizations of all sizes to invest in data encryption and cybersecurity.
In this context, the Encryption software solutions have taken a center stage, to protect the sensitive data from unauthorised access and ensure that if it is stolen by the attackers it remains unreadable and useless for them.
Interestingly, the data encryption tools are also evolving to include post-quantum cryptography (PQC), ensuring long-term data confidentiality. Experts like Nigel Smart warn that businesses must be “crypto-agile” to respond quickly to emerging vulnerabilities. In 2025 and beyond, AI-powered encryption isn’t just innovation, it's a necessity. The future of cybersecurity is intelligent, automated, and always one step ahead.
This blog explores how artificial intelligence is giving encryption tools a major upgrade, along with the future advancements of data encryption software that will be playing a remarkable role to safeguard the organization's valuable data assets.
What is Data Encryption?
Data encryption is a security practice where sensitive data is converted into an unreadable, coded format leveraging mathematical algorithms which makes it meaningless for a person unless a secret key or password is used to access it. Encryption acts as a major obstacle for threat actors with criminal intentions, making sure data intercepted or retrieved without authorisation remains inaccessible.
At a time when data is seen as a critical resource, encryption and its ability to act as a digital lock guarantees that no one uses this precious asset without rightful access. This process not only protects the data itself but also ensures that customers as well as business partners feel comfortable and safe working with your organisation. It also helps businesses strengthen the customer trust through this demonstration of dedication to the privacy of their information.
The data encryption market is likely to touch USD 40.2 billion by 2032. Data safety and privacy is the primary concern for many today and the only way to tackle this is to invest in the best data encryption software.
What is Data Encryption Software?
Data encryption software is a program that uses code to prevent unauthorized third parties from gaining unlawful access to an organization’s digital assets. Data Encryption software takes plain text, like a text message or email, and scrambles it into an unreadable format called ciphertext. This applies to both the information stored on company machines, as well as that being shared among users. To unlock the message, both the sender and the recipient have to use a “secret” encryption key that is a collection of algorithms that scramble and unscramble data back to a readable format.
Types of Data Encryption Software Classification
An encryption key is a series of numerics utilized to encrypt and decrypt data. Encryption keys are created with algorithms, and each key is random and unique.
There are two main types of encryption systems that are widely adopted today, that are: symmetric encryption and asymmetric encryption. Here’s how they differ.
Symmetric Key:
The symmetric key is a single cryptographic key derived with the help of encryption algorithms for both encrypting and decrypting data. The terms to understand here are ciphertext which is the encrypted data, and plaintext which is decrypted data.
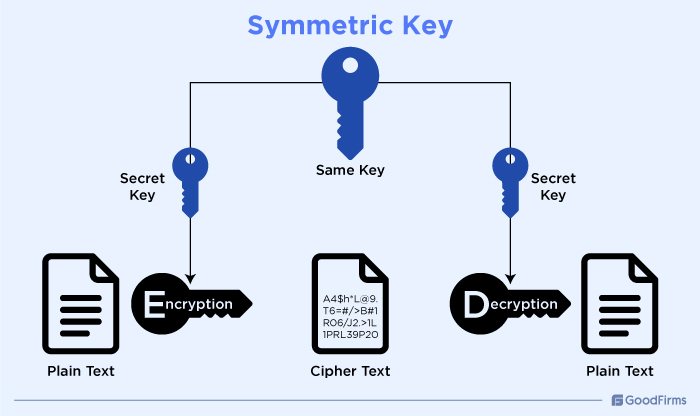
Benefits
- Speed: The symmetric encryption algorithms work faster than asymmetric ones, which makes them suitable for encrypting large amounts of data.
- Efficiency: The symmetric encryption consumes less computational power which makes it ideal for devices with limited resources.
Common Algorithms:
- Advanced Encryption Standard (AES): It is widely considered as one of the most secure symmetric encryption methodologies. The AES supports various key lengths of 128, 192, or 256 bits.
- Blowfish: It is known as a fast block cipher which encrypts data in 64-bit locks with unmatchable speed and flexibility.
- Triple DES (3DES): It applies the DES algorithm three times to each block for an enhancement of the original Data Encryption Standard (DES) for increased security.
Asymmetric Key:
The asymmetric key includes two pairs of keys: a public key and a private key. The public key is given to the users, while the private key is kept confidential having access only to the owner. With this asymmetric key algorithm, users can only encrypt a file or communication utilizing the public key. To decrypt the encrypted file or communication can be only done with the private key. For this reason, asymmetric encryption is considered as the most superior alternative to encoding.
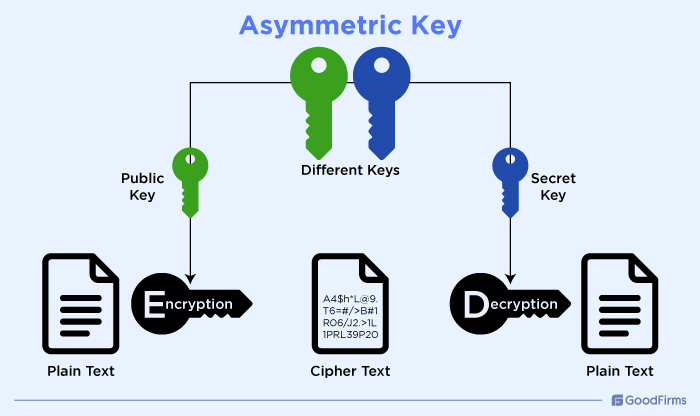
Benefits
- Enhanced Security: As the asymmetric encryption involves two keys, even if a public key is compromised, the private key remains secure and reduces the risk.
- Key Distribution: Asymmetric encryption makes it fearless when it comes to public key distribution to the users without any risk of exposing their private keys.
Common Algorithms
- RSA (Rivest-Shamir-Adleman): This is one of the first public keys, widely utilized for secure data transmission.
- Elliptic Curve Cryptography (ECC): It offers smaller key sizes, making it more efficient in terms of computational power which is similar to RSA security.
- Digital Signature Algorithm (DSA): It is used for digital signatures in helping to ensure the authenticity and integrity of messages
How is Encryption Software Redefining Enterprise Cybersecurity?
- By preventing unauthorized access to confidential data including financials, employee records, customer data
- By ensuring compliance with data privacy regulations such as GDPR, HIPAA, DPDPA, CCPA
- By providing secure communication channels emails, file sharing, cloud storage)
- By protecting brand reputation by reducing the risk and impact of data breaches
How is AI-Powered Data Encryption Software giving a major upgrade for Enterprise Cyber Security?
In the modern digital communication era, AI is playing a significant role in meeting the challenges of digital assets against cyber threats. It has become crucial for sectors of businesses to implement these technological advancements into their systems for enhanced security, data protection and adaptive solutions.
AI-powered encryption software provides a groundbreaking advancement in data encryption and cybersecurity leveraging the abilities of artificial intelligence and machine learning to strengthen data protection. AI data encryption tools use machine learning algorithms which help to continuously detect, analyze and adapt to new cyber threats. Moreover, the combination of AI and machine learning makes it an incredibly dynamic and proactive defense mechanism against unauthorized access or data breaches and providing an extra layer of defense in data encryption systems.
Additionally, many of these data encryption platforms are also integrating post-quantum cryptography to prepare sectors of businesses for the next generation of cyber threats. It helps businesses be more resilient, proactive, and future-proof security posture meeting the evolving demands of today’s digital enterprises.
Top Enterprise Encryption Use Cases from Leading Brands:
Top brands are using data encryption software to protect businesses today and preparing for tomorrow’s quantum-era threats. Let us analyze a few of them:
#1. Cloudflare: Post‑Quantum Encryption Built into Zero Trust
Cloudflare has recently integrated post‑quantum cryptography into its Zero Trust Network Access platform, offering end-to-end quantum‑safe connectivity from browsers to corporate web applications. Support will extend to all IP protocols by mid‑2025. This ensures businesses secure their sensitive traffic without needing to overhaul every application, especially valuable for finance, telecom, and government clients.
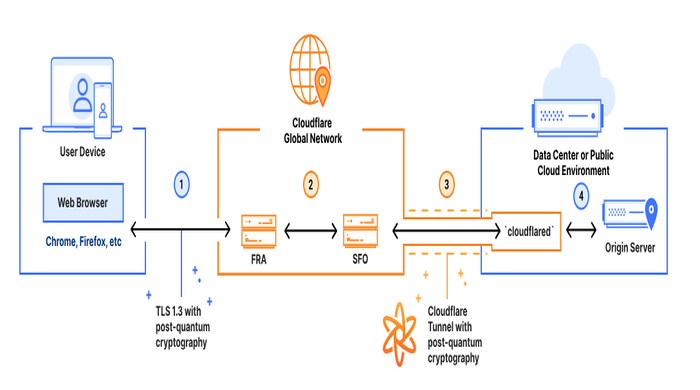
Source: Cloudfare
Highlights:
- There is built-in quantum resilience at no extra cost
- It has collaboration with banks, ISPs, governments
- Today, over 35% of human‑generated traffic already enjoys PQ security
#2. Google Workspace: Client-Side & End-to-End Encryption for Enterprises
Google has launched a simplified end-to-end email encryption feature powered by client-side encryption, which lets enterprises control encryption keys and protect data even from Google itself . It helps companies in regulated industries can now secure emails and calendar data with minimal IT overhead, reducing risk while preserving compliance and control.
Source: Google Cloud
Key details:
- There is no need for manual certificate exchange
- The admins can retain key control and revoke access
- The rollout expanding to non‑Gmail recipients later in 2025
#3. Google Digital Sovereignty: Quantum‑Ready Encryption Key Management
At Google Cloud Next 2025, Thales unveiled its CipherTrust Cloud Key Management platform designed for quantum-safe client-side encryption in Google Workspace. The solution enables encrypted emails and documents controlled entirely by enterprise key policies. It benefits the organisations to gain precise regional control over encryption keys crucial for compliance (e.g. HIPAA, ITAR), IP management, and cross-border data policies.
"Client-side encryption gives us the next level of privacy, to ensure integrity within the journalistic process. This allows us to guarantee a higher level of security for our journalists, and to protect our sensitive content," said Sacha Morard, Chief Technology Officer at Groupe Le Monde.
.gif)
Source: Google Cloud
Key benefits:
- It supports various enterprises in achieving data sovereignty
- It allows deployment across Gmail, Drive, Docs, Calendar
- It is aimed for general availability by end of 2025
The Future of Encryption
As cyber threats continue to advance, and the technologies behind encryption are also advancing to provide even more secure transmissions:
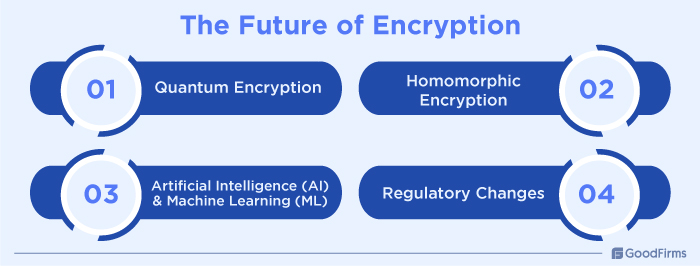
1. Quantum Encryption:
Quantum encryption, sometimes referred to as quantum key distribution, is a technique that derives the above unbreakable keys with the help of quantum mechanics. Totally different from the classical approach, it forms noninterceptable and nonduplicable keys without the recipient’s knowledge. In the upcoming bounds and leaps, quantum encryption brings vast progress to the field of cybersecurity.
2. Homomorphic Encryption:
Homomorphic Encryption allows computation on data with features that preserve plaintext computation, keeping sensitive information private as it operates. Although in its initial stage, homomorphic encryption can revolutionize data security, perhaps saving cloud computing from failure in dangerous, untrusted environments.
3. Artificial Intelligence (AI) and Machine Learning (ML):
AI and machine learning will disrupt current encryption schemes through process automation, detection of vulnerabilities, and optimization of algorithms for improved performances. These will also improve threat detection through pattern-recognizing abilities in the encrypted data.
4. Regulatory Changes:
The regulatory and legal landscapes of encryption are very dynamic. The new laws that are set up can drive change in business strategy, including the application and management of encryption. Being aware and adapting to such change is most important in compliance and security.
Wrapping Up: The need to address vulnerabilities and prepare for a post-quantum world.
Today, cyber threats have become more advanced, which has made businesses to rely less on the outdated security models, and start investing in AI-powered encryption software to enhance and redefine enterprise cybersecurity. It includes threat detection in real-time to post-quantum readiness, these data encryption tools with latest features and new advancements offer the modern enterprise demands that is agility, speed and resilience.
Modern businesses that are willing to stay ahead in the digital world should start adopting the AI-driven and crypto-agile encryption solution to reduce the risk of threats, prevent sensitive data, meet regulatory requirements and build long lasting relationships with customers.




