Although it may seem like a warning, the headline and tips in this blog will fundamentally change your cloud computing approach.
Cloud computing often brings significant risks to businesses compared to traditional IT environments. Insecure APIs, data exposure due to misconfigured storage, weak encryption, mismanaged accounts, weak passwords, unpatched software, incomplete security settings, open ports, and poor network configurations are some of the reasons that could trigger vulnerabilities in cloud environments. Undetected threats and lack of insights can lead to business workflow obstruction. Network detection and response (NDR) is a modern network security solution that uses real-time analysis to monitor and permeate network traffic and the end-point layers.
As more businesses are adopting hybrid and multi-cloud approaches, the shared responsibility between the teams many times gets blurred. NDR can be the right solution to gain visibility across clouds, deliver modern application architectures, and improve operational efficiency. Network Detection and Response tools or NDR can seamlessly monitor network traffic and detect and respond to attacks that target cloud infrastructures. Businesses can have enhanced insight into threats, contextual visibility through behavior analytics, and automatic threat response. The prime benefit of NDR tools is that companies can get a unified AI-driven security monitoring facility.
The following sections will explain in detail the top 10 benefits of using NDR in a cloud environment, apart from other major topics on this subject.
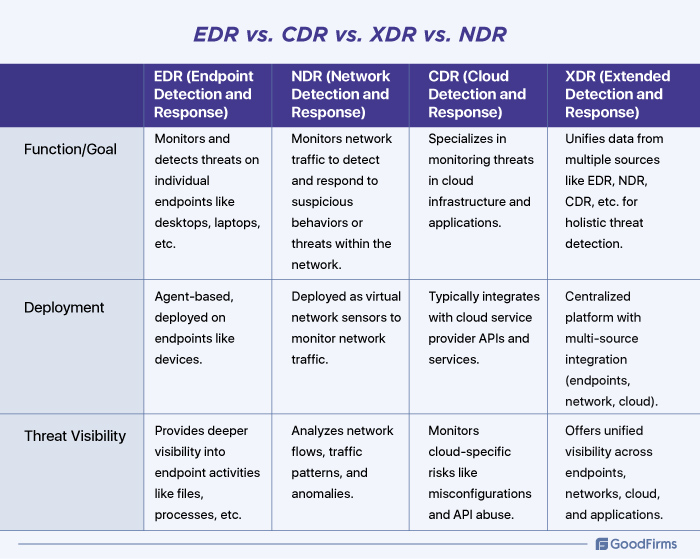
Before we go further on NDR and its benefits, let us see the difference between EDR, NDR, CDR, and XDR.
EDR vs. CDR vs. XDR vs. NDR
Although Network Detection and Response (NDR), Endpoint Detection and Response (EDR), Extended Detection and Response (XDR) and Cloud Detection and Response (CDR) are technologies to detect and respond to threats, individually, they are unique and have their own set of goals to achieve. Let’s understand the basic differences between these:
What are the Most-Common Network Threats in Cloud Environments?
Cloud environments offer enormous perks to businesses; however, these advantages of the cloud also make it vulnerable to security threats and breaches. Here are the top network threats in cloud environments:
.jpg)
Lack of Visibility and Human Error
Lack of visibility and human error are the most common network threats in the cloud environment. This is because most businesses still do not realize the importance of robust network security measures in the cloud environment and have limited monitoring of user activities and threats. Studies indicate that through 2025, 99% of cloud security failures will be due to the customer’s fault (human error).
Data Breaches
Sensitive data stored in the cloud, including customer information and intellectual property, are at risk of exposure/breach due to insecure configurations or unauthorized access, resulting in significant financial and reputational damage for businesses.
Account Hijack
Attackers can gain unauthorized access to cloud accounts through weak credentials, phishing, or social engineering. This allows them to manipulate or steal data, bypassing security measures. Moreover, deficient networks are at high security risk due to insider threat with negligent or malicious insiders accessing and exposing sensitive business data.
Denial of Service (DoS) Attacks
Attackers overburden and disrupt the cloud and its resources with excessive traffic, slowing down or crashing services. This results in downtime and affects service availability, damaging business reputation.
Unprotected APIs
APIs or application programming interfaces are widely used to interact with cloud services. However, poorly designed or unprotected APIs are common entry points for attackers, exposing sensitive data or system controls.
Malware
Attackers inject malicious code into cloud applications, leading to data corruption, unauthorized access, and many other harmful effects on the cloud environment.
Misconfigured Cloud Settings
In complex cloud infrastructures, misconfigured permissions, storage, and cloud network settings can lead to unintentional exposure of sensitive data and enable unauthorized access. Such threats increase with increasing complexity of cloud processes and user errors in growing businesses.
Container Vulnerabilities
With the rising use of technology, new types of threats are rapidly emerging, including container vulnerabilities. Misconfigurations, outdated images, and insecure container registries commonly expose containers to attacks, including privilege escalation allowing elevated access in a compromised container and lateral movement risk where the attacker can easily move from one compromised container to another, putting even the host system at risk. Malicious elements exploit these flaws to compromise workloads, access sensitive data, and disrupt services.
Ransomware as a Service
According to IBM, ransomware is another common cyberthreat, involved in 20% of all cybercrime incidents. The emerging trend of ransomware as a service (RaaS) enables cybercriminals to deploy ransomware without technical expertise, posing serious network threats in cloud environments. Using RaaS, attackers can easily infiltrate systems, encrypt data, and disrupt business operations. Cloud-specific network threats associated with RaaS include compromised credentials, misconfigurations, and lateral movement, requiring comprehensive security measures and regular backups to combat the evolving threat.
Top 10 Advantages of Using NDR in Cloud Environments
The Global network detection and response (NDR) market size is likely to touch USD 8.97 Billion by 2032, as per the latest reports.
Prioritizing attacks and stopping them in real-time demands powerful features from NDR solutions. Most modern and next-generation network detection systems come with sophisticated AI-based threat detection, analysis, and real-time attack response features which makes it ideal for a safe cloud computing approach.
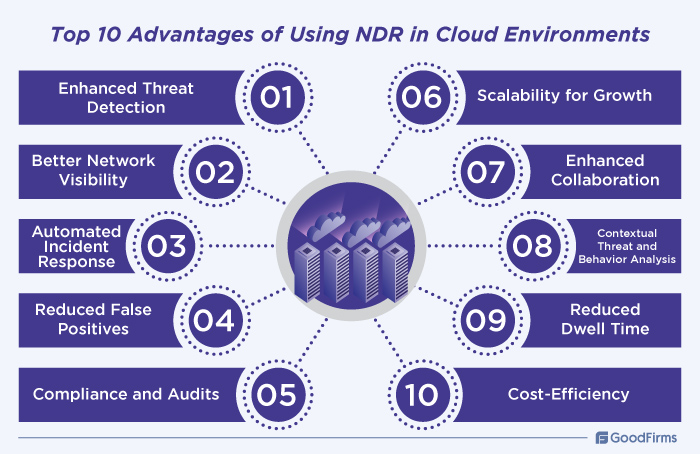
NDR leverages network metadata to monitor network traffic for detecting potential threats in real-time. It can detect anomalous behaviors, patterns, and cyber threats in the network using AI, ML, behavioral analytics, and more, with enhanced precision. NDR or network detection and response solutions offer in-depth security benefits for cloud environments, providing robust threat detection, improved incident response, scalability, and a lot more, making it an essential tool for businesses looking to secure their cloud infrastructure effectively. Here are the top 10 benefits of leveraging NDR in the cloud:
Enhanced Threat Detection
NDR offers real-time and advanced analytics, machine learning (ML) capabilities, and artificial intelligence for deep analysis to monitor cloud network traffic instantly and continuously. By analyzing behavioral patterns and anomalies, NDR can detect a wide range of threats, including zero-day attacks, insider threats, and lateral movements within the network, which can be challenging to identify with traditional security tools.
Better Network Visibility
Businesses typically use multiple cloud platforms or hybrid setups, which complicates network monitoring. NDR offers unified visibility across different environments, including hybrid and multi-cloud environments, ensuring consistent monitoring and threat detection. This holistic view helps enhance overall security and makes it easier to manage complex cloud setups, ensuring no blindspots. It also allows businesses the flexibility to safeguard their network while leveraging the cloud setup that best matches their business needs.
Automated Incident Response
Cloud environments require quick response to threats to minimize potential damages and costs for businesses. NDR solutions provide real-time alerts and insights, enabling security teams to quickly investigate and respond to incidents. Advanced NDR tools further enable automated response actions like isolating compromised resources to reduce the progression and impact of an attack.
Reduced False Positives
Traditional security tools typically produce high volumes of false positives, causing confusion and overwhelming the security teams. NDR leverages ML to differentiate between normal and suspicious activities, reducing false positives and enabling more accurate threat detection. This allows security teams to focus on genuine threats without being distracted by false alerts, saving significant time and resources for businesses.
Compliance and Audits
Many industries, like finance and healthcare, have stringent compliance requirements, including data protection norms and security monitoring mandates. NDR helps businesses meet these requirements by continuously monitoring and documenting network activities. The insights and reports provided by NDR can simplify audits and allow businesses to demonstrate diligent adherence to regulatory standards.
Scalability for Growth
As businesses grow and expand their cloud footprint, they face increasing challenges in terms of security. NDR solutions are designed to scale seamlessly with cloud environments, allowing better handling of larger volumes of data and more complex traffic patterns without compromising on threat detection capabilities. This flexibility ensures continued cloud network protection as the business grows, supporting long-term business continuity and success.
Enhanced Collaboration
NDR solutions typically offer collaboration features like incident-sharing and cross-team communication tools, which facilitate better coordination between security teams. This collaboration is particularly valuable in cloud environments where network configurations and security responsibilities may be split across teams. Improved communication and collaboration between various stakeholders of cybersecurity enables faster, more coordinated responses and overall enhanced security processes for businesses.
Contextual Threat and Behavior Analysis
NDR helps detect abnormal behaviors across workloads. Moreover, it provides context around detected threats, including the assets involved, the severity of the threat, its potential impacts, and more. Contextual threat detection and behavior analysis helps security teams prioritize responses based on the potential impact on critical assets, leading to more efficient and effective incident handling. AI-powered NDR solutions facilitate accurate and timely detection of high-risk threats using contextual threat and behavior analysis, creating a revolution in the network security arena for cloud environments for businesses.
Reduced Dwell Time
Dwell time or the time between an attack’s occurrence and its detection is a significant and critical parameter in network security. A longer dwell time increases the potential damage an attacker can cause to the cloud network. NDR’s continuous monitoring and rapid detection capabilities help reduce dwell time, limiting an attacker's ability to exploit vulnerabilities in the cloud environment, providing better opportunity to the security teams to take appropriate action and shrink damages, and ensuring robust security.
Cost-Efficiency
Network detection and response (NDR) enhances resource optimization and overall cost-efficiency in cloud environments by automating threat detection, reducing manual monitoring, minimizing response times, and preventing breaches. Further, its precise anomaly detection helps reduce false positives saving significant time and resources. Moreover, early threat identification prevents costly breaches and minimizes operational disruptions, optimizing cloud resource allocation and utilization and shrinking overall costs for businesses.
Future of Network Threats and Detection in Cloud Environment
As more and more businesses are switching to cloud-based infrastructure, platforms, and applications, the future of network threats and detection in cloud environments is becoming a crucial concern. While the cloud offers agility, scalability, and cost-effectiveness, it also introduces unique challenges and vulnerabilities that cybercriminals can easily exploit. As businesses migrate their data and operations to the cloud, the threat landscape is evolving rapidly, demanding a serious approach to detection and response strategies.
Apart from threats like distributed denial of service (DDoS), account hijacking, data breaches, API abuses, and container vulnerabilities, attackers are now misusing automation to identify and exploit vulnerabilities faster than ever before through Ransomware-as-a-service (RaaS) and AI-driven malware.
Cloud environments are dynamic and distributed, with resources constantly being created and removed, adding to security risks. Moreover, with rapidly emerging technology-powered security threats in the cloud environment, there is an increasing need for new and innovative detection methodologies, tools, and technologies to better identify vulnerabilities in the cloud environment. Here are some emerging trends, practices, and technologies that will rule the future of network threats and detection in cloud environment:
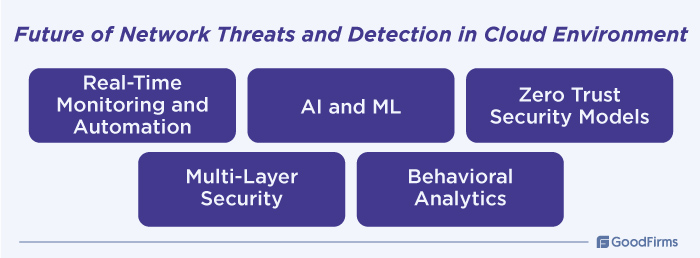
Real-Time Monitoring and Automation
Future detection strategies will leverage automation, real-time threat intelligence, and behavior-based monitoring to respond promptly to emerging threats. Businesses must adopt adaptive and resilient security architectures in combating the growing complexity of cyberattacks.
AI and ML
While attackers are leveraging AI to evade threat detection, making it further challenging to match with the rising risk of security threats in the cloud environment, AI and ML powered NDR solutions will continue to enhance threat detection in the cloud. These technologies enable real-time analysis of vast data sets, identifying subtle anomalies and potential threats, and will help predict and neutralize threats proactively.
Zero Trust Security Models
The zero-trust model assumes no user or device can be trusted by default, whether inside or outside the network. It enforces strict access controls, identity verification, and continuous monitoring, reducing the likelihood of unauthorized access and lateral movement within the cloud systems. Businesses must embrace such models to ensure better network security over years to come.
Multi-Layer Security
Multi-layer security combining identity verification, encryption, micro-segmentation, and regular audits creates robust, multi-layered defenses. This approach helps minimize the attack surface and ensures better protection against complex threats.
Behavioral Analytics
Behavioral analytics leverages AI and ML to identify unusual patterns in user and system activity, enabling early detection of threats like insider attacks, account takeovers, and data exfiltration. In the dynamic cloud environment, this proactive approach can help businesses adapt to evolving threats, offering higher precision and speed over static, signature-based detection methods for robust security.
Wrapping Up
Leveraging NDR solutions in a cloud environment offers significant advantages to businesses aiming to enhance cloud security. NDR provides real-time visibility into network traffic, enabling the early detection of threats and anomalies. Moreover, NDR uses advanced analytics, machine learning, and behavior-based monitoring to help identify potential risks with higher accuracy that traditional security tools commonly fail to detect.
NDR enhances threat mitigation by automating response actions and reducing dwell time for attacks. Furthermore, NDR ensures compliance with security policies and regulatory requirements while seamlessly integrating with existing cloud architectures. Ultimately, NDR strengthens an organization’s security structure, ensuring proactive protection in an increasingly complex cloud ecosystem. Businesses must thus embrace NDR solutions to safeguard their cloud networks, shrink damages due to security breaches, build trust among various stakeholders, and rise to new heights.






