The reliance on computer networks has increased tremendously in modern work environments. Most information is created and shared via computer networks. The network system gets highly complicated, with thousands of workstations in large organizations and several hundred in small companies. Ensuring centralized management, the right security configurations for each workstation, access control integrity, protection parameters, and exact cybersecurity protocols on all systems can be extremely daunting.
Organizations must also deal with multiple levels of cybersecurity awareness among their employees. Not all employees are on the same page regarding network security knowledge. An uninitiated employee with poor cybersecurity skills can cause the whole network security layers to fail. Cyber attackers are constantly looking for such weak spots, unsecured networks, systems that can be easily compromised, and vulnerabilities to target network servers that contain valuable data and sensitive information.
This necessitates companies to deploy policies, practices, and tools to secure many devices and prevent unauthorized access to network-based resources. Network security software can protect companies from malicious cyber attacks and secure the integrity of their networks and data sets. Network administrators can use network security applications to oversee and protect their organization’s complex architecture.
Why is it crucial for organizations to preserve their network security?

Cyber intruders try to attack and read data packets in server environments. They exploit vulnerabilities, weak authentications, and code glitches to launch an attack that can cause a denial of network service or modification of an organization's existing security protocols.
Such serious problems can incur huge losses for businesses. Therefore, securing the complete network chain to thwart cyber attackers' nefarious attempts is crucial to protecting networks' reliability and usability.
Network security is crucial for:
- Protecting precious data and making sure data is accessible only by authorized employees.
- We maintain the accuracy, speed, and reliability of networks and network-based resources.
- Ensure that the data is legitimate throughout its use and is not corrupted by the insertion of spoofing channels.
- Meeting the regulatory requirements and compliance by protecting user data.
- Preventing any downtime, ransomware situations, and damage to costly software applications
What is Network Security Software?
Network security software is an application designed to protect, secure, manage, and preserve network and network-based resources. It consists of various tools that enhance the security parameters of an organization's networks and establish coercive control over data transmission over networks. It eliminates all potential network cyber threats, vulnerabilities, and loopholes that unscrupulous attackers can exploit.
How can organizations establish standardized network security protocols with the help of network security software?

The network security mechanism is a complex process that, according to the International Telecommunication Union (ITU), involves the fulfillment of three objectives for cybersecurity: Availability, confidentiality, and Integrity. Instead of these objectives, network security experts have developed multiple protocols to establish secure data transmission over networks. However, it cannot be done manually. Network security experts rely on applications to manage all aspects of network protection.
A network security software makes it super easy for businesses to ensure all core network vitals such as:
Client-Server Authentication:
Employees often use web applications and emails that require connecting to a server. Data is also transferred while accessing servers, making them vulnerable to attacks. Network security software's client-server authentication process makes it mandatory for all users to prove their identity to access servers. This can be achieved by all or one of the methods, such as password-protected access, encrypted data transmission, digital verification certificates, and more.
Firewalls
Network security software can establish next-generation advanced Firewalls that erect a barrier between a trusted network and unauthorized networks. Firewalls foil any infiltration attempt.
Email security
The email security module of a network security tool protects email servers and gateways from security breaches such as sophisticated phishing campaigns, malware links, and other means to deceive recipients and senders.
Anti-virus and anti-malware tool
Network security software applications have built-in modules to protect networks from viruses, ransomware, Trojans, and other malware that can infect system computers and trigger network glitches.
Network segmentation protocol
Network security software classifies traffic into various segments to enforce security policies more efficiently.
Access control
Deploying a network security tool that assigns layered access to users, devices, and traffic channels and keeps potential threats in check can supervise network access. Network administrators can define user roles and limit access to sensitive devices or layers.
Application security
An organization uses multiple software applications (many of them from third-party vendors) to run its operations. Attackers may exploit the vulnerabilities in those applications to access your system networks. Network security software creates a defensive mechanism to ensure your networks remain safe from indirect infiltration attacks.
Network analytics
Network security tools come equipped with indicators that can detect abnormal network behavior, such as a sudden surge in server loads or unsolicited HTTP requests. Such behavioral analytics can provide valuable information to trigger predictive remedies.
Data loss prevention
Data loss prevention (DLP) tools in network security applications prevent the unprotected upload, forwarding, or printing of critical information, which can lead to data compromise.
Intrusion prevention systems
An intrusion prevention system (IPS) constantly scans network traffic to block malicious activities. Network security tools can recognize potential threats by identifying globally recognized common attack tactics.
Mobile device security
With organizations using mobile applications and employees downloading them on their devices, mobile phones have become the first targets for malicious cyber attacks. Network security tools can configure mobile connections for safe network usage.
VPN
Network security tools can set up virtual private networks that use SSL (Secure Socket Layers) to authenticate communication between endpoint devices and networks.
Web security
A network security solution can block suspicious websites, bad gateways, websites with malicious links, and other websites to secure internet surfing and ensure a safe web experience.
What types of cyber attacks can be prevented by Network security software?
Network Security software can prevent all types of cyber attacks:
- Eavesdropping refers to Data theft when information is transmitted over a network. Also known as sniffing, it attempts to steal information by connecting devices (laptop, mobile, desktop, etc.) and an unsecured network.
- Data modification: Also known as MDA (Modification data attack), it refers to a situation when cyber attackers delete, modify, or interrupt data with malicious intent by gaining unauthorized network access.
- Denial-of-service attack: When attackers make the data or network resources inaccessible for legitimate users or data owners.
- DNS spoofing: DNS stands for Domain name servers. When attackers alter the DNS records to divert and redirect traffic to an unreliable website for vested interests, it is called DNS spoofing or DNS cache poisoning.
- Phishing: Phishing attacks are intended to steal sensitive user data such as login details to various applications, credit card credentials, passwords, etc. A cyber attacker poses as a legitimate entity and tricks the user into clicking on a link sent through email, message, contact page, etc. If clicked, the link installs malware on the device, and the user loses control of the device.
- Smurf attack intends to render the networks inoperable by flooding them with ICMP (Internet Control Message Protocols) packets. The server load is increased to a limit that the networks cannot handle anymore and become inoperable.
- Man in the middle: In this attack, an intruder hacks and alters the communication between two parties.
- Virus attacks: Virus attacks occur when malicious code or files attach themselves to network resources and documents and try to infect or damage them. The virus is used to steal valuable data and sensitive information, such as passwords, so the network can be misused. Viruses such as ransomware encrypt all system files, and attackers ask for money to release them. Recently, sophisticated Android mobile ransomware has evolved. The increased usage of office apps on mobile devices is a serious threat.
Other benefits of Network Security Software:
- Compliance: Network security software can help your business achieve regulatory standards and avoid government action.
- Protects assets: Your company owns many resources, proprietary data, and sensitive and confidential information. You can ensure these valuable assets are safe and secure with network security tools.
- Smooth workflows: Any sudden network outage can be devastating for your business. Protecting networks from all cyber risks ensures smooth workflows and unhampered operations.
- Improved productivity: Securing networks with network security software increases productivity by limiting employees' access to healthy websites and not allowing them to open an unsecured one.
What are the Features of Network Security Software?
- Threat detection: Network security software protects your network's usability by early threat detection, including viruses, targeted server attacks, ransomware, malware, snooping attacks, etc.
- Threat Mitigation: Network security software takes necessary actions to mitigate all potential threats by preventing threat elements from entering the networks or taking countermeasures to eliminate them.
- Controlled Network access: Network security software effectively secures all entry points and stops network access without authentication.
- Security Layers: Network security tools build multiple layers of security with rule-based policies and controls. The scrutiny of multi-layered security blocks any malicious attempt to exploit the network.
- Network discovery: Network security applications can automatically detect, discover, and monitor all network assets, such as computers, laptops, mobile devices, servers, printers, and routers.
- Network scans: Network security system continuously scans networks for missing patches, threats, malicious files, security loopholes, etc.
- Third-party application monitoring: Your robust networks can be compromised if third-party apps with access to them have security flaws. Network security tools monitor third-party applications for missing security standards and patches.
- Known issues monitoring: Network security systems monitor globally recognized vulnerabilities and known threats.
- Compliance regulations: Network security software solutions ensure network health meets regulatory standards such as PCI DSS, HIPAA, GDPR, etc.
- Reporting: Network security tools have features to generate automated reports about Network performance, which is also essential for compliance requirements.
Other features:
- Firewalls: Set up a firewall according to your discretion, needs, and customization required.
- Malware detection: Detects ransomware, software bugs, trojans, distributed attacks, and many more.
- Network mapping and visibility: It prevents unauthorized mapping and discovery.
- Monitor firewall policies and manage changes
- Audit firewall security
- Analyze firewall logs to find critical anomalies in bandwidth usage
- Endpoint security
- Network Access Control
- Traffic analysis
- Set Rules
- Monitor the user behavior of firewall administrators.
- Accelerate security incident response
- Investigate security alerts
- Send Encrypted network traffic
- Detect anomalies in the network
- Behavioral analytics for a sudden change in network performance
- Easy network segmentation for increased performance
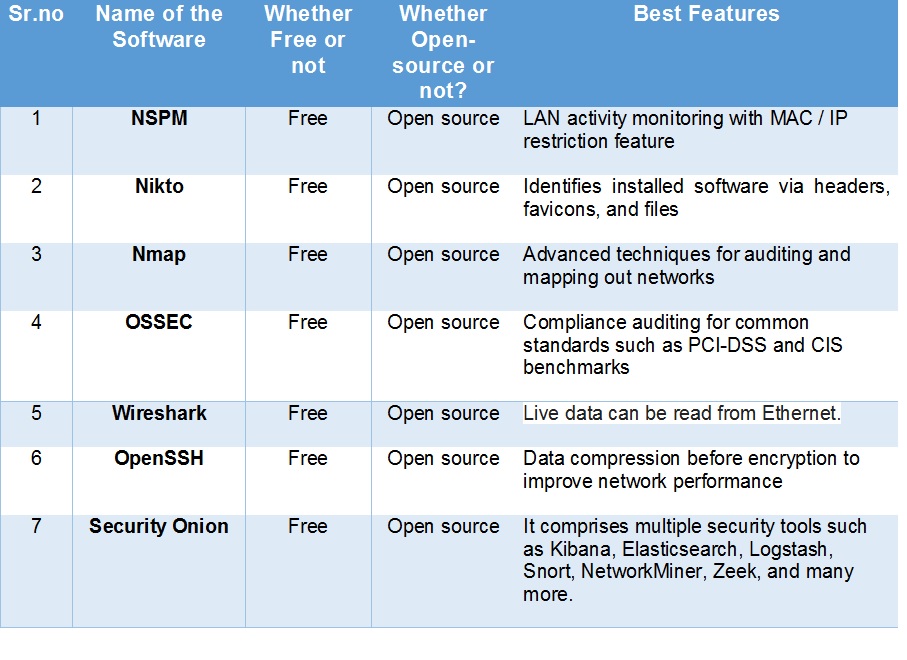
The list of 7 best Free and Open Source Network Security Software
- NSPM
- Nikto2
- Nmap
- Ossec
- Wireshark
- OpenSSH
- Security Onion
Comparison table of 7 best free and open source Network Security software:
1. NSPM
NSPM is a free and open-source network security software that assists network and system administrators in creating, monitor, and manage network security policies and underlining firewall access rules. It is easy to deploy a software application and can be installed on PCs or servers as a standalone application. It requires only a browser to run the application and set configurations. The application is certified under the GNU General public license. You can download and start using the application to secure your networks.

Key Features:
- Network interface information
- Current operational status
- Current system summary and basic health controls
- Incoming and outgoing connections with features for direct blocking
- LAN activity monitoring with MAC / IP restriction feature
- Rules list with color display and author comments
- Action buttons to enable, turn off, move, duplicate, edit, or delete rules
- Standard protocols and rule targets
- Source and destination interfaces
- Advanced filtering options
- Global security policy settings
2.Nikto2
Nikto2 is a free and open-source network security software and web server scanner that performs thorough tests against web servers for potential threats, including over 6,700 potentially dangerous files/programs. It also detects outdated server versions and version-specific problems. It regularly checks server configurations, index files, HTTP server options, and plugins. It checks and provides information about security flaws present on network servers. It is free for personal and commercial use under the GNU GPL license.

Key Features:
- SSL Support
- Full HTTP proxy support
- Auto-pause at a specified time
- Checks for outdated server components
- Scan multiple servers
- Identifies installed software via headers, favicons, and files
- Checks for common "parking" sites
- Save reports in plain text, XML, HTML, NBE, or CSV
- Host authentication
- Checks Guess credentials for authorization
3. Nmap
Nmap is free and open-source network security software used for network auditing. It accomplishes multiple tasks, such as monitoring host or service uptime, filters/firewalls, network discovery, Password audit, Sniffers, Web scanners, Packet crafters, and more.
Key Features:
- Advanced techniques for auditing and mapping out networks
- Discovers the OS and version detection
- IP filters, firewalls, routers, and other obstacles
- Can scan vast networks of thousands of machines
- Supports all types of OS such as Linux, Microsoft Windows, OpenBSD, Solaris, IRIX, FreeBSD, Mac OS X, Sun OS, Amiga, HP-UX, NetBSD, and more
- Scans servers for potential threats
- Host Authentication
4. OSSEC
OSSEC is a free and open-source network security software with powerful intrusion detection features. It also comes with other security tools such as an analysis engine, log analysis, file integrity monitoring, real-time alerting, centralized policy enforcement, Windows registry monitoring, rootkit detection, and active response. It runs on most popular operating systems, including macOS, Linux, Windows, and FreeBSD. It is distributed under the terms of the GNU General Public License (version 2). It is downloaded over 500,000 annually and deployed for server protection and firewall monitoring.
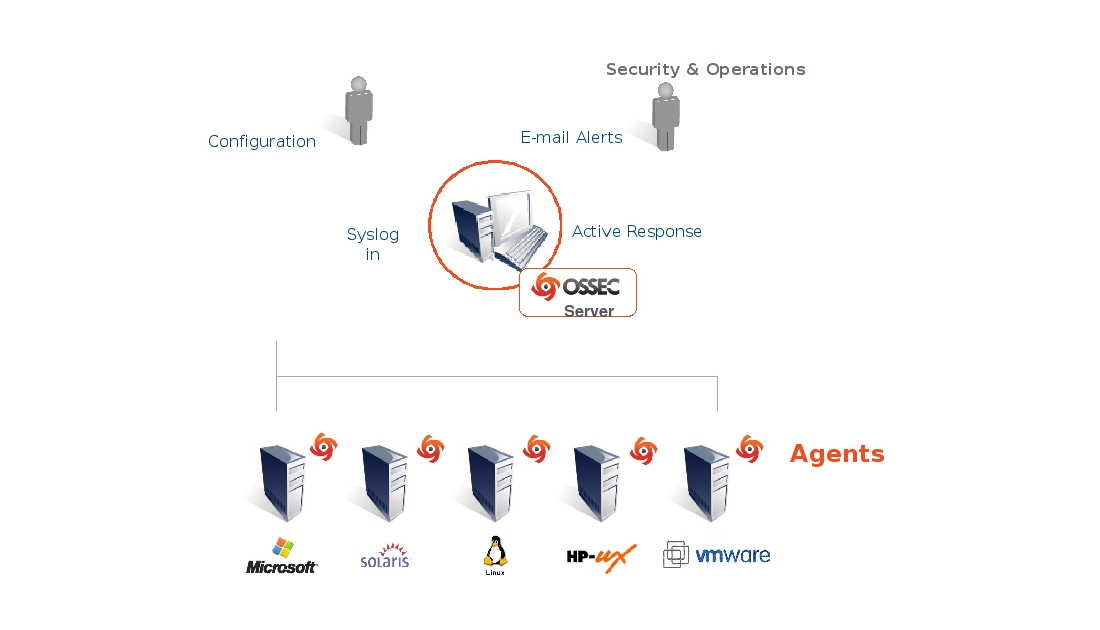
Key Features:
- Log-based Intrusion Detection (LIDs) monitors data from multiple log points in real-time
- Rootkit and Malware Detection to detect malicious applications
- Responds to attacks and modifications on the system in real-time
- Security through multiple mechanisms, such as firewall policies, self-healing actions, and integration with CDNs for enhanced security
- Compliance auditing for common standards such as PCI-DSS and CIS benchmarks
- File Integrity Monitoring (FIM) and Windows registry settings in real-time not only detect changes to the system but also maintain a forensic copy of the data as it changes over time.
- Collects system information such as installed hardware, software, network services, etc
5. Wireshark
Wireshark is a free and open-source network packet analyzer that measures what's happening inside a network. Network security engineers can use it to analyze and troubleshoot security problems. It lets network administrators check what is happening with their network at a microscopic level. It runs on multiple platforms, including Windows, Linux, macOS, FreeBSD, Solaris, and NetBSD. It is accessible under the GPL license.
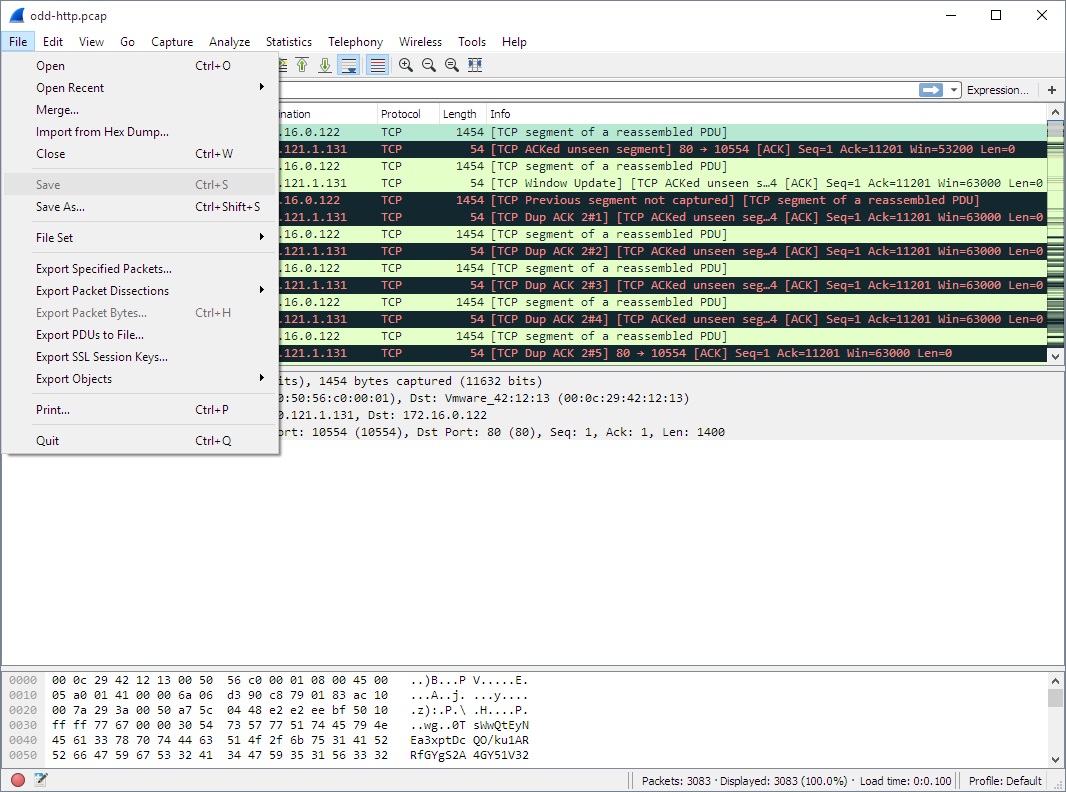
Key Features:
- Filter and search packets
- Display packets with very detailed protocol information.
- Save packet data captured
- Live capture and offline analysis
- Search for packets on many criteria
- Colorize packet displays based on filters, and Coloring rules can be applied
- Deep inspection of hundreds of protocols
- Live data can be read from Ethernet
- Decryption support for many protocols
6.OpenSSH
OpenSSH is a free and open-source network security tool that assists network admins in securing their networks. It encrypts all network traffic to eliminate connection hijacking, eavesdropping, and similar attacks. OpenSSH possesses several authentication methods and security configuration options. It provides encryption for network services via the SSH protocol.

Key Features:
- Encryption to protect against spoofed packets
- Prevents snooping and inserting of malicious commands
- Port forwarding to secure internet applications like POP
- Strong authentication (public keys, one-time passwords)
- Protects against IP spoofing, fake routes, and DNS spoofing
- SFTP client and server support
- Data compression before encryption to improve network performance
7. Security Onion
Security Onion is a free and open-source network tool for enterprise security monitoring, threat hunting, and log management. It comprises multiple security tools, such as Kibana, Elasticsearch, Logstash, Snort, NetworkMiner, Zeek, and many more.
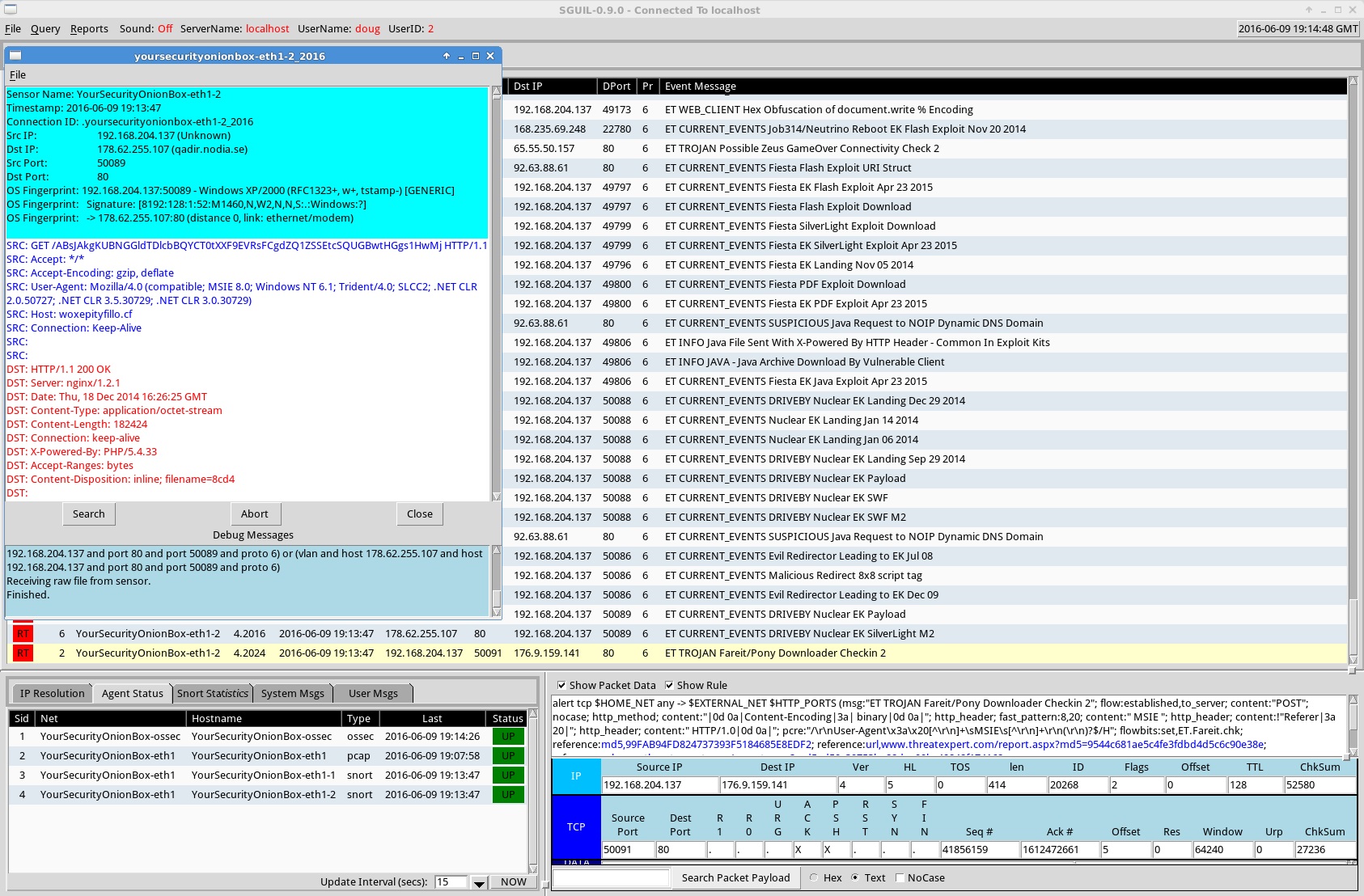
Key Features:
- Access Control
- Compliance Management
- Intrusion Detection System
- Real-Time Monitoring
- Reporting & Analytics
- Security Assessment
- Threat Management
- Vulnerability Management
Any of the above top 7 free and open-source network security software can be used by organizations to secure their networks and build impenetrable firewalls. If you need more stringent protection parameters, efficiency, and high-end security features, you can add SandBlast Network to your list. SandBlast is one of the most popular industry-grade network security software solutions available. Let us see its features in detail:
Sandblast Network
Sandblast Network security software helps network administrators neutralize unauthorized access or denial of network resources. It protects organizations from potentially harmful traffic. Sandblast provides complete protection from phishing attacks and malware intrusions. It uses behavioral detection with advanced artificial intelligence to capture any unevenness in data. It also applies full attack remediation capabilities.
Key Features:
- Malware prevention on email and web
- Protects user activity across email, web, and networks for robust security against multiple attack vectors
- CPU-level emulation that stays resistant to invasive attacks
- OS-level inspection
- Malware DNA analysis
- Uses data science and AI to protect user activity across the web
- Threat extraction for email and web
- Compliance and reporting
- Enhanced Ransomware
Conclusion:
To round it off, businesses can choose from any network security software discussed in this article to relieve themselves from network security-related worries. Apart from the free network security software discussed, AlienVault USM, FireMon Security Manager, GFI LanGuard, Naverisk, Vectra, and Tenable.io are other network security applications you may choose to secure your IT infrastructure.
We welcome your views about the article. Please comment in the section below. Share your feedback with us if you have previously utilized any of the free network security softwarementioned above.
If you wish to analyze the features of any other free network security software or software categories, visit Goodfirms' software directory page.






