Over the years, the crypto market has gained a notorious reputation for being volatile, perpetually uncertain, and catastrophic, so much so that investing in it is considered financial suicide by many.
Well, to put things in perspective for you, 2022 will go down in crypto history as the year that was fraught with frauds, malware, and bankruptcy; the fortunes of many vaporized —an obvious cue for savvy crypto investors to reevaluate their financial plans.
But then, the fact remains: crypto enthusiasts, more or less, are cavalier to cryptos’ inflection points and cold turkey crashes. Much to the dismay of skeptics, the cryptos advocate positively believes in the power of virtual money based on its previous track record of rewarding early adopters with millions in days.
All told, to ensure that events like those of 2022 never happen again, it is essential to look for tried and true ways to secure your crypto assets—for instance, a cold wallet. If you are planning to develop a crypto wallet this year for your business, weigh the pros and cons of a cold wallet and a hot wallet minutely before roping in a blockchain developer.
The article highlights the most significant crypto hacks of 2022 and how “cold wallets” are safe against hacks and thefts.
Notorious Hacks that Shook the Crypto Space in 2022
Well, as mentioned above, 2022 was reported to be the worst year in crypto history, with $3 billion stolen at the last count. The Ronin bridge hack, in particular, caught the world's attention.
As the BBC reports, thousands of people lost their money, and some even their life savings, when this gaming-focused, Ethereum sidechain bridge was hacked by a Northern Korean hacker group called Lazarus.
The hacker group stole $625 million from this bridge built by Sky Mavis that powered a popular play-to-earn (P2E) non-fungible token game Axie Infinity. Gamers used to save digital coins on the Ronin network by playing the Axie Infinity game.

Gamers used to save digital coins on the Ronin network by playing the Axie Infinity game that reported a whopping $625 million hack
The surprising part, though, is it took almost a week for the attack to be discovered by law enforcement officials. So far, the officials have managed to recover about $30 million of stolen funds, and the Binance cryptocurrency exchange was able to freeze nearly $5.8 million. But then sadly, the fact remains that most of the assets are still under the hackers' control.
Wormhole Token Bridge, a known cross-chain crypto bridge that connects, among many others, Ethereum, Solana, and Avalanche, lost $321 million. The money has yet to be recovered, so the hack has made the attacker rich by $320 million. Jump Trading tried to get the bridge back into operation by injecting Wormhole with 120,000 ETH.
Nope, it doesn't stop here, though. Nomad Bridge suffered a loss of $190 million, while Wintermute, a decentralized platform, reported a loss of $160 million. As if these weren't enough, another high-profile hack was reported from the Binance exchange in October 2022 for $570 million.
The point isthat having a protection mechanism in place will help shield crypto exchanges and Crypto Wallets from hacks.
Until we implement these protection mechanisms, the only safe wallet that crypto users should rely on is Cold Wallet.
Cold Wallets are Safe Because They are Offline Wallets
Investors buy digital currencies like Bitcoin or Ether through a crypto exchange and then keep that currency on that platform. And, sure, these digital exchanges do all that they can to keep your cryptos safe and secure. But then, these cryptocurrency exchanges are not immune to hacks. Consider the recently bankrupted crypto exchange FTX.
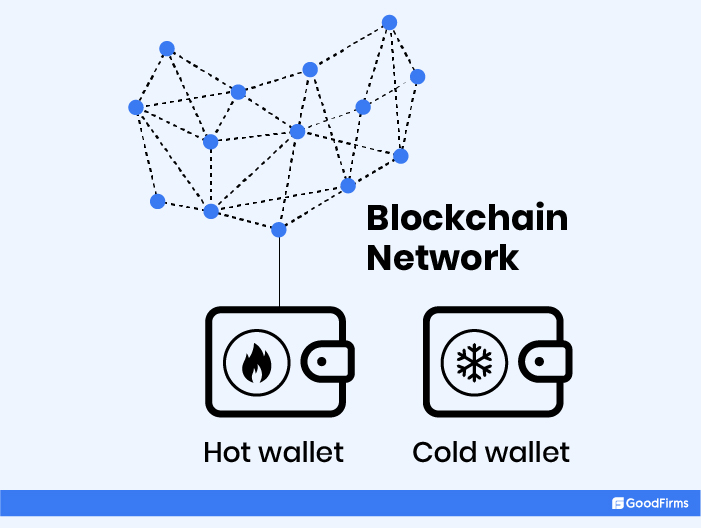
This is when cold storage - Hot Wallets and Cold Wallets - comes to your rescue. In fact, one of the safest ways to protect some or all of your bitcoins and other altcoins is to store them in a wallet, just like you keep your cash and credit cards in physical wallets.
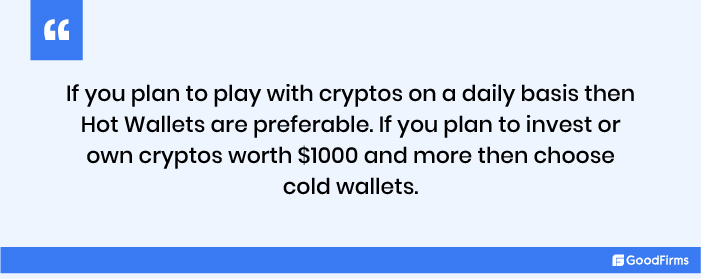
However, as per bitcoin experts, cold wallets are considered much safer than hot wallets. Unlike the latter, the former is not connected to the internet, making it hacker-proof and, at the same time, earning it the nomenclature of an "offline” wallet. The bottom line is always to store your bitcoins in an offline, or "cold," wallet.
And being an offline wallet, it’s not vulnerable to viruses that are known to be on your network-connected computer.
More critical, cold wallets are typically open source. This means the community can attest to its safety standards instead of companies doing for it.
Also, it includes software that helps the user view the portfolio without using his private key.
But if cold wallets are so secure and hot wallets are prone to attacks, why do we need hot wallets in the first place?
Hot Wallets - Online Wallet and thus Honeypot for Hackers. Despite its insecure nature, users can't ignore it
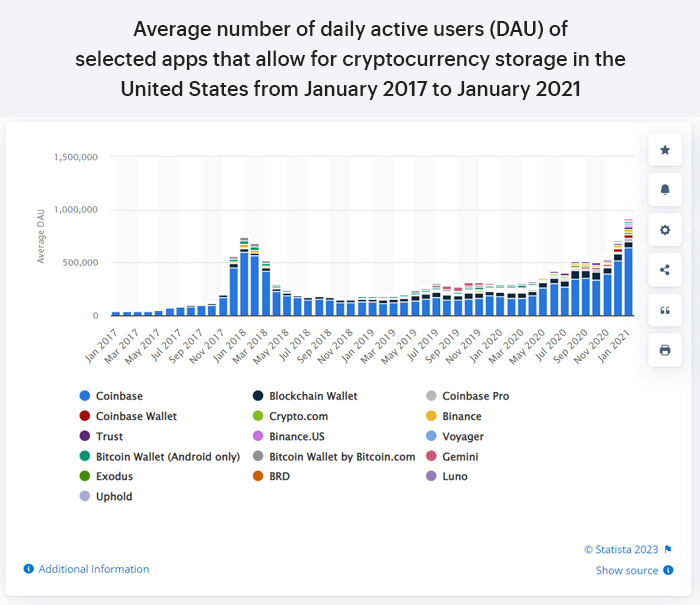
Hot wallets and cold wallets are both popular ways of storing your crypto. And if you look at the Statista graph for the most popular cryptocurrency storage apps in the U.S. alone, Coinbase - a San Francisco-based hot wallet app- is downright the leader. (But again, if you are counting on security measures, Coinbase is not ideal because it’s online.)
My point is, despite the growing popularity of cold wallets as a secure wallets, overly optimistic and enthusiastic investors will invariably prefer hot wallets.
Wait, aren't hot wallets insecure because they're online and thus a tempting target for hackers? Yes, they are. But then again, there are many good reasons why investors are more inclined toward hot wallets than cold wallets.
1. Convenient: Unlike cold wallets, hot wallets are always connected to the internet. That is, the user does not need to take any additional steps to connect the hot wallet to the internet, which makes the coin transfer process extra convenient for traders and daily cryptos players.
2. Cost: Hot wallets are generally available for free. While free options are also available in cold wallets, hard wallets are available in the $100 to $200 range.
3. Security: Hot wallets compared to crypto exchanges are pretty secure and use public and private keys to ensure a frictionless flow of transactions. However, its primary advantage, being online, that is, could prove disadvantageous as it makes it vulnerable to hacking compared to cold wallets.
Long story short, cold and hot wallets are an indispensable part of the crypto ecosystem. Both need to exist in parallel for the smooth running of the crypto market. Hot wallets are a reliable form of wallet for crypto traders and individuals who prefer to make quick online payments through cryptocurrencies. In contrast, cold wallets are the safest bet for those who intend to store their cryptos as an investment.

Speaking of storing investments for a long time, how do these cold wallets compare to more traditional investment options like Banks?
Storing Cryptos in Cold Wallets Versus Cash in Traditional Banks
Strictly speaking, traditional banks inevitably refund the stolen money if your savings or current account information is compromised. However, in the crypto market, things could be exceptionally unsafe. As mentioned above, fortunes get evaporated in a fraction of a second, and money recovery has negligible scope.
In a broader sense, if your crypto account gets compromised or your token is stolen, the owner will be unable to recover most of their coins.
If you ask why? Simply because digital currencies are decentralized. Banks or government officials don’t support digital currencies.
This means that although the crypto market isn’t nearly as secure as banks, those willing to risk investing in cryptos have no option but to move away from banks and rely on crypto exchanges and personal wallets.
This means savvy crypto investors must be doubly sure of the security measures that could be undertaken to protect their tokens. Hence, Cold wallets are the need of the hour for crypto investors as they provide a safe and secure storage medium for Bitcoin and other altcoins.
All this talk about crypto storage, security, and wallets inevitably makes one question, ‘How do cold wallets work? And what makes them hack-proof?’
But before diving into these questions, let's take a moment to step back and understand how crypto transactions work as well as the role of public and private keys play in the process.
The Use of Public Keys and Private Keys for Crypto Transactions
When creating a crypto wallet, you are given public and private keys. Both these keys are an indispensable part of crypto transactions.

Public keys
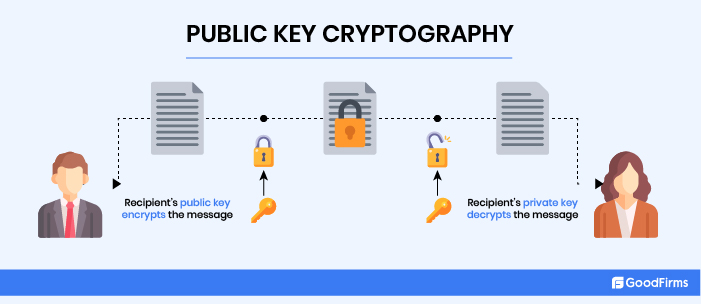
A public key is used for sending and receiving cryptocurrencies in your cold wallets.
Public keys function like your email address or, say, your account number. You share your public key with anyone to send and receive crypto in the same way that you share your email address to receive an email.
Private Keys
A private key is not shareable. It’s like an email password (alphanumeric characters) that you avoid sharing with anyone. You use the private key to verify (sign) transactions and prove ownership of your address. For example, if someone sends you bitcoins, you will need the private key to unlock the transaction and confirm that you are the Bitcoin owner. The bottom line is that you will only have access to your funds through a private key.
In short, the public key encrypts transactions, while the corresponding private key decrypts them. The encrypting-decrypting technology is referred to as public-key cryptography, or PKC, or asymmetric cryptography.
The private key is in the company's custody if you keep your cryptos in exchange wallets (WazirX and Binance) or maybe with a custodian. In other words, the company would control the funds.
Storing Private Keys
Hot wallets can easily be hacked, as private keys are stored online. Your cryptocurrencies are secure as long as your private keys are safe. The moment the keys get stolen or hacked, your crypto holdings are gone, maybe forever. So please write it down and store it in a safe place. Don’t take a screenshot of it, as digital copies can be hacked.
Now that we have a working understanding of public and private keys, let's take a look at how cold wallets ensure your crypto’s safety.
How Cold Wallets Work?

As stated previously, a "cold wallet" is an offline, physical device that cannot connect to the blockchain and complete the transaction independently. That is, in order for a user to conduct a transaction using a cold wallet, it must be connected to an internet-connected device. However, the internet connection does not threaten the private key.
Let’s see how it works:
Cold wallet storage can be essentially divided into two parts:
a) Cold Wallet Core
b) Cold Gateway
The functions of the Cold Wallet Core and the Cold Gateway are worlds apart. While a cold wallet core operates offline and is air-gapped, a cold gateway is connected online. A transaction occurs in the internet-connected cold gateway within the cold wallet; however, the transaction signing takes place offline in the cold wallet core. Once the transaction is signed, it’s broadcast online through the cold gateway.
Let’s understand the cold wallet transaction process through an example of TREZOR, a cold wallet. TREZOR being a hardware wallet, is offline and air-gapped simultaneously. This is to say that TREZOR is hacker-proof. So to initiate transactions in TREZOR, the user needs first to install the TREZOR mobile app, as it’s connected to the blockchain.
The entire cold wallet transaction process via TREZOR wallet can be summarised in four steps.
- The user launches a transaction on the TREZOR app.
- The app requests confirmation from the cold wallet.
- The TREZOR wallet signs the transaction using a private key.
- The app completes the transaction and broadcasts the signed transactions to the blockchain network.
How Are Cold Wallets Safe and Keep Thieves and Hackers Away?
Hot wallet transactions are carried out using a single online device. The wallet generates and stores private keys, gets the transaction digitally signed with the aid of the private key, and then broadcasts the signed transaction to the network.
The problem? When the signed transaction is broadcast online, a hacker crawling the network gains access to the private key used in the transaction.
Cold storage takes care of the issue by transferring the online transaction to the offline mode. In other words, the transaction is initiated online; however, the signing part is done within the device, such as a USB drive, a compact disk or a hard drive, or an offline computer, (in cold wallet core), using a private key before it's uploaded to the blockchain using a crypto bridge (in a cold gateway).
As the private key is not connected to the server during the signing process, online hackers are unable to access the key. Given the added security measures, it’s not at all easy to transact cryptos on cold storage devices and in fact considered a hassle as opposed to hot wallets.
6 Examples of Cold Storage for Crypto Investors
Though different types of cold storage are available, Hardware Wallets are more popular. Contrarily, USB drives are risky and not ideal in the long run. Let’s look at the five types of cold storage devices that crypto investors can use.
1. Paper Wallet
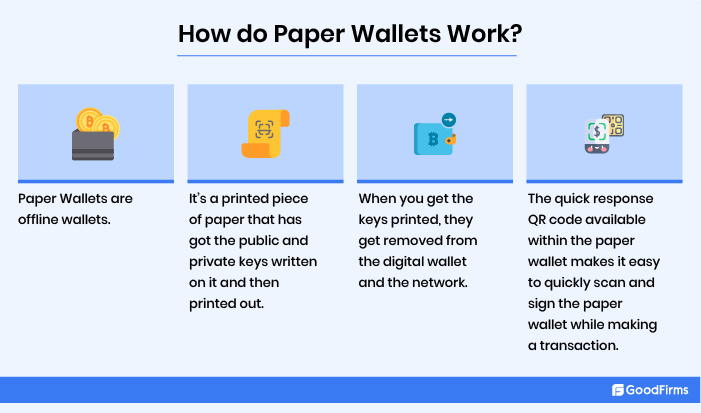
Paper Wallets are one of the most commonly used forms of cold wallets. It's a printed piece of paper with public and private keys written on it that's then printed out. For instance, in the case of a bitcoin paper wallet, a bitcoin holder can take a printout from the bitcoin paper wallet tool online with the help of a printer.
When you get the keys printed, they get removed from the digital wallet and the network. A hacker can only get close to your keys if your paper gets stolen, damaged, or considered illegible.
The quick response QR code available within the paper wallet makes it easy to quickly scan and sign the paper wallet while making a transaction with hot wallets.
If you plan to store your cryptos using this method, make sure you come up with a safe box or any other secure storage method to keep your paper wallet safe.
2. Hardware Wallets
Another example of a cold wallet is a hardware wallet that stores users’ private keys in hardware devices such as advanced flash drives. They are like portable wallets that can be plugged into the computer.
Besides an offline device, a hard wallet can even use a smart card to generate private keys offline. For instance, the Ledger USB Wallet uses a smart card to store private keys.

Further, a hardware wallet is not just a storage device. Because your private key is built into the device, you don't need to copy or display it on the screen when performing a crypto transaction. You have to click a button in the wallet. Copying the key, in all likelihood, could lead to potential attacks.
Furthermore, Hardware wallets facilitate direct trading from your wallet rather than transferring assets into other online digital wallets first.
All told, just like a paper wallet, the device or the smartcard should be securely stored, as any damage or loss could terminate the users' access to bitcoins. Private keys are kept offline on a computer and in a Chrome-based app.
3. USB Drive
If a hardware wallet is out of your budget, you can use a conventional USB flash drive to store your private cryptographic keys. But this won't be as secure as a hardware wallet, and you can't conduct transactions efficiently. Simply put, it can only store your private key offline. So use a USB drive only temporarily.
4. Sound Wallets
Sound Wallets are not that popular because they are expensive compared to other wallets. In this case, the private keys are stored as an encrypted video on CDs or 7-inch vinyl. The encrypted private key is converted into a short sound file (less than a minute long) and may sound like white noise to outsiders. However, you can access the keys using a spectroscope app that will help you decrypt the information from the sound file.
According to Sound Wallet’s Theodore Goodman, vinyl will outlast memory cards, paper wallets, and CDs as their condition deteriorates. Most importantly, the vinyl doesn’t give the impression that it can store such confidential information, so it always remains safe from hackers.
5. Deep cold storage
You can compare this storage method to storing your smuggled heist money. All you do in this case is dig a six-foot hole in the ground and bury your cold wallet. Before placing the cold wallet underground, put it in a hardware container. Another way out is to store your cryptocurrencies in a vault belonging to a third party, which requires multiple steps to access.
6. Offline Software Wallets
Offline software wallets are yet another obscure type of cold storage. The functions and features are almost identical to those of hardware wallets; however, they are more complex and complicated, so they are not a favorite of non-technical users. An offline software wallet is divided into two platforms: an offline wallet to store your private keys and an online wallet to store your public keys.
New transactions are generated on the online wallet but remain unsigned. The user address is sent to the receiver or the sender on the other end. The transaction gets signed on the offline platform with a private key. The signed transaction is then sent to the online wallet, which displays to the network that the transaction is complete. The private keys remain safe as offline wallets never come into contact with the blockchain network. Electrum and Armorya are the best examples of offline software wallets.
Aside from cold wallets, crypto experts have identified additional security measures that could be implemented on different platforms to reduce the prevalence of crypto hacks.
Additional Security Measures Identified by Crypto Experts
In addition to cold storage use, additional strict protocols have been put in place to ensure that events like that of 2022 are a thing of the past. So what could these strict protocols be?
- First, get the smart contract's code audited over and over again by known third-party vendors. And every time the code is updated, it should be re-audited. Once the audit is over, the code should be run through the community to inform them about the issues and the solutions adopted to address them.
- Second, real-time proactive monitoring of transactions on different platforms to detect any suspicious activity. For instance, a sudden spike in transactions comprising massive amounts directed to the same address or interaction with blacklisted accounts, and so on
- Finally, setting up a response system in advance so that the team behind the protocol can immediately jump into action and stop the hackers dead in their tracks when a hack happens. Or, if the platform/system is already in the middle of a hack, then immediate intervention can prevent additional loss of funds.
According to coindesk article, “This Was the Worst Year for Crypto Hacks. Here’s How 2023 Can Be Better, “Community-led security monitoring helps secure the overall crypto ecosystem by incentivizing such monitoring and allowing anyone to have a window into the operational health.”
All things considered, there isn’t a blanket solution to all the hacks and exploits. Having that said, a protocol comprising frequent audits, real-time operations monitoring, and clear-cut attack response plans will minimize such crypto hacks and exploits. Or maybe such hacks can be halted or reversed within an hour or two if not minutes. It takes days, sometimes weeks, for the attack to be discovered.
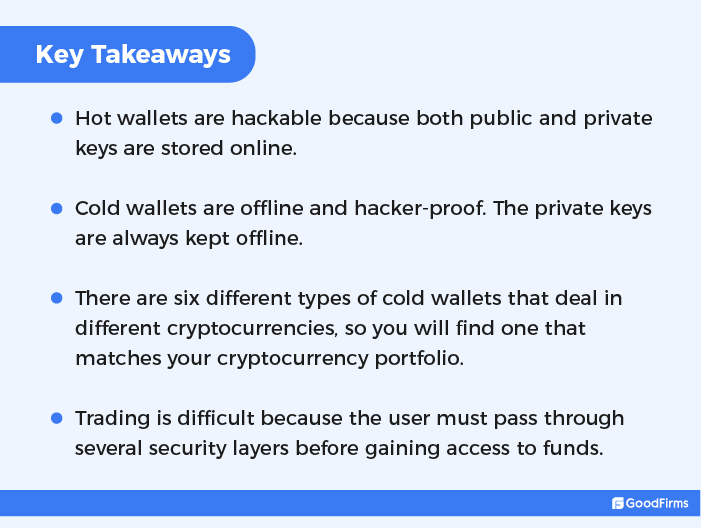
Takeaways
Hot wallets are not secure because public and private keys are stored online. Cold Storage, on the other hand, is offline and hack-proof because the private keys are always kept offline and thus never fall into the hands of hackers. Additionally, six kinds of cold wallets are available that deal in different cryptocurrencies. You’ll always find one to keep in your cryptocurrency portfolio. However, there’s one significant limitation regarding cold storage: trading is difficult as the user must pass through several security measures before gaining access to the funds.