The world today is more digitally interconnected. Most organizations, whether governments, enterprises or NGOs, are increasingly relying on technology to effectively connect and conduct their operations irrespective of their physical location. Remote desktop protocol (RDP) is a big breakthrough in that aspect, as it allows users to take control of any computer system across distance, access critical files, and collaborate seamlessly from anywhere. The increasing acceptance of remote work, globalization, quick access to technical support, and BYOD (bring your own device) policy are driving factors for the adoption of remote desktop software.
But, as attackers are picking up their pace, not only understanding the risk is critical, but also knowing the tactics to mitigate the risk is of utmost importance. This is both for the business leaders who are strategizing, and for the tech leaders who are operating.
“RDP abuse occurred in 90% of incident response cases in 2023, and continued to dominate with 84% involvement in 2024 ,” says the Active Adversary Report from Sophos.
No system is infallible. Missing on MFA (multi-factor authentication), compromising on the credentials, extended dwell time, AD (active directory) and RDP (Remote desktop protocol) facilitates attacks. Here, in this blog we will discuss in detail the risks of RDP and the ways to mitigate it by using the most secure remote desktop software.
With the rise of hybrid work models and digital transformation, remote desktop software is a critical medium for many individuals and enterprises to manage their work and continue business without any interruption. But during the same period, many remote staff had their first encounter with hackers invading their system, and since then, incidents of unauthorized access to remote desktop software have been on rise.
The nature of remote desktop software enabling access to protected resources via an external network places them at higher risks. Remote desktop software has diverse use cases like remote recovery and data backup, support and maintenance, managing VPS (Virtual Private Server), system setup and configuration, and so on. It continuously exchanges data on its network and hackers envision it as a gateway to fulfill their malicious intent. Cybersecurity and Law enforcement agencies such as CIS, CISA, MS-ISAC, and the FBI have been reporting misuse of remote access software to target organizations.
Demystifying security risks associated with remote desktop software and addressing them without affecting the user's experience is the top priority of remote desktop software providers. But, despite all the security measures and preventive steps, the fear and uncertainty always loom on the user's mind as hackers have become more sophisticated in their attacks. For instance, hackers can invade your remote desktop tool and use deep fake technology to pretend to be your colleague or supervisor. Simply sharing a small info with them could turn out catastrophic for end-users when not having proper awareness about the protocols for remote desktop software. So, why do hackers primarily target remote desktop software? How to neutralize their cyber attacks? This blog covers it all.
How Does Remote Desktop Software Become Vulnerable to Security Threats?
Remote desktop software has gained popularity due to its diverse applications like gathering data on network and devices, remote recovery and data backup, support and maintenance, managing VPS (Virtual Private Server), system setup and configuration, etc. Because it interacts with sensitive databases and IT infrastructures, it has become the prime target and an entry point for hackers. Hackers use various tactics to deceive the security system and exploit weak zones in the remote desktop tool.

Living off the land (LOTL) cyber attacks
Remote desktop software is designed to access the end-user system, and when someone allows permission to access their system, it is not flagged as a threat. Taking advantage of this, cybercriminals target remote desktop software networks, and as soon as permission for access is granted, it enters the victim’s system unnoticed. This type of attack is known as living off the land (LOTL) attacks, where cyber criminals target victims using tools already existing in the system and do not create malicious code or files. LOTL attacks are among the most common global cyber threats that are used in around 80% of attacks to evade detection by security tools like antivirus.
Bypass firewall rules
Many remote desktop software users share files using end-to-end encryption and bypass firewall rules, thinking that it is safe. Hackers take advantage of this loophole and download malicious files on the victim’s system.
Sell access to multiple hackers
Once the weak zone has been identified in the network, some hackers sell the network access to other cybercriminals, making it more vulnerable.
Unrestricted RDP port access

Out of all the vulnerable spots, port 3389 remains a major attack vector in 2025 for hackers. It is a Remote Desktop Protocol (RDP) for Microsoft Windows that provides an easy way to establish remote connections; hence hackers mostly target this port based on assumptions that it may be in use. Usually, administrators keep this port open to establish a connection with remote desktops, but hackers exploit it using different brute force attacks.
Multiple login for SaaS apps
The use of multiple SaaS apps could be a potential risk if users are not following security best practices. Users juggling between multiple user logins for SaaS apps often use passwords that are easy to predict or hack.
Disable security tools
Among the different methods hackers use to prevent the detection of their unauthorized access, a major one is disabling security tools. There are various ways hackers search and disengage security tools, like deleting registry file keys, interrupting normal security processes, disabling regular updates, terminating the tools by force, tampering artifacts utilized by security tools, etc.
Powershell cyber attack
Powershell attack also known as zero-footprint attack does not leave any traces of hacking. Powershell is a powerful scripting language used by hackers to deliver malware, data exfiltration, and ransomware deployment. Its fileless approach and ability to execute commands directly in the memory makes it untraceable. Its ability to run WinRM remotely makes the tool more appealing to hackers and intruders into the system.
Human-induced weakness
Human-induced weakness or vulnerability is a term used to describe poor permission access control and weaknesses. Organizations that do not follow strong security policies for remote desktop software access can easily become targets to hackers. Hackers can use social engineering techniques to gain access to the victims’ system.
How to prevent Remote Desktop Software cyber threats?

System threat modeling
By developing system threat models for remote access servers and resources used by the remote desktop software, the administrator can identify possible risks associated with it and take counter-actions accordingly. It is a structured representation of all the information that could affect the security of the system.
Account lock policies for brute force attempt
TCP 3389 is a standard port for remote access and hackers usually target them using brute force attacks. They use trial and error techniques to hack the login credentials. The best way to neutralize this effect is by implementing account lock policies, in which the account automatically gets locked once hackers put wrong passwords beyond set limits. Another way is to change the default listening port TCP 3389 to something else but make sure you update the Firewall rules with the new port. This strategy is helpful to hide remote desktop software from hackers scanning the network to target default listening port TCP 3389. This strategy is helpful, but relying on this alone may not guarantee hackproof remote desktop software. It is preferable to use other security measures along with it.
Audit network
Audit remote desktop software and configurations on devices on the network to identify the current use of software and any unauthorized access to the software. Also, establish a policy for patch management for software directly accessed through the internet, making them less vulnerable to cyber attacks. In 2025, behavior-based detection and AI-powered threat monitoring are becoming essential for securing RDP environments, where fileless attacks and remote login abuse remain persistent threats.
Smart card authentication
One of the common reasons for security breaches is the failure of identity management. Smart card authentication is an alternative to passwords. Companies can store employees' credentials on the smart card in the form of a private key and a certificate. So, when employees want to access remote desktop software, they need to first authenticate their identity through this smart card. Smart card authentication is a popular choice of security teams to secure the system endpoints and reduce the risk of identity theft. Owing to this, the global smart card market is anticipated to reach USD 20.3 billion in 2025, and is expected to expand to USD 30.6 billion by 2030.
Implement strong security policies
Cyber threats in remote desktop software can also be prevented by enforcing strong security policies like two-factor authentication, strong passwords, and enabling event logging on a regular basis. Other measures to prevent security breaches include implementing single sign-on for SaaS apps and enforcing security controls like on-screen watermarking for sensitive applications.

Microsegmentation and zero trust
In microsegmentation, the computer network is partitioned into smaller or sub-networks to limit the movement of hackers within the application infrastructure if they succeed in getting unauthorized access. Implementing sub-networks with more robust security policies further makes the network inaccessible to hackers. Through microsegmentation, security teams can easily monitor and respond to network traffic in real-time for better system security. It perfectly fits into a Zero-trust model and when combined with microsegmentation, can give robust security.
Use jump host
A jump host is an intermediary server or device that acts as a gatekeeper between two networks. One can access the destination server only after the jump host allows access. It is a security hardened machine that provides a single point of entry to the server using firewalls and a secure channel.
VPN Tunnels - Shift Toward Zero Trust Network Access (ZTNA)
Traditionally, one of the most effective ways to protect remote desktop access from unauthorized access has been the use of VPN tunnels. One of the main reasons behind high VPN usage is that VPN tunneling allows 22% professionals to safely access work files. A remote access VPN connects remote users to the organization’s system through an encrypted tunnel. VPN tunnel is used to transfer data to the destination safely over untrusted networks.
However, as cybersecurity threats evolve, so do the solutions. According to Gartner Predicts--"By 2025, 60–70% of organizations are expected to move away from VPNs in favor of zero-trust solutions. ZTNA (Zero Trust Network Access) allows access only after verifying user identity, device posture, location, and risk level, enforcing the principle of least privilege."
Reverse proxy server and forward proxy
Both reverse proxy servers and forward proxy servers are used to protect devices connected to private networks. Forward proxy is majorly used by universities and large corporations to block students or employees from accessing certain websites. A reverse proxy server is particularly more useful in defending remote desktop software against cyber attacks. A reverse proxy sits between the internet and the internal server. So, when users call a request, it does not connect to the main server, but it first connects to the proxy server, which then forwards this request to the main server or backend server. Thus, it denies direct access to backend operating systems. The proxy server can implement various authorization and authentication methods to allow access to only authorized users. In addition to traditional proxies, cloud-based secure web gateways (SWGs) and cloud access security brokers (CASBs) are being integrated with reverse proxy setups to provide enhanced monitoring, data loss prevention, and inline threat protection in hybrid work environments.
Remote desktop security best practices
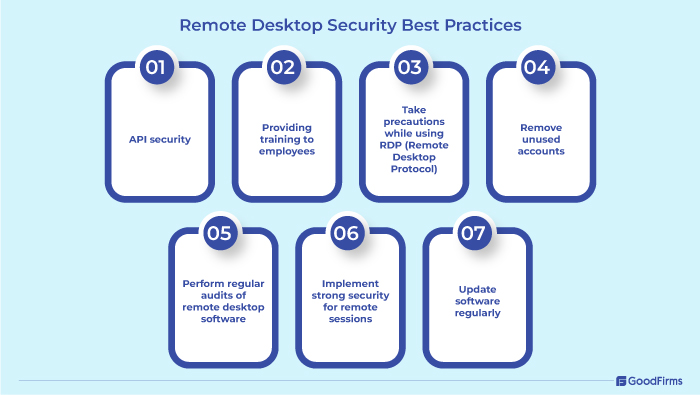
Along with the above desktop preventive measures, if users follow remote desktop security best practices, it can be pretty helpful in addressing security concerns for remote desktop software.
API security
API is used to establish communication between the remote desktop system and the client, but it is also vulnerable to security threats. In fact, according to an API security report, 60% organizations experienced some API related cyber threats in the last two years. Many remote desktop software, while using API for remote access, often ignore its safe access and fail to include an adequate authentication process. As a best practice, it is advisable that users follow safe authentication processes like multi-factor authentication, monitoring API usage, scanning API regularly for suspicious activity, implementing rigorous validation for all API inputs, etc.
Providing training to employees
Implementing strong security measures without providing training to employees to safely access remote desktop software is meaningless. Employees using remote desktop tools should be given some basic training tips like regularly updating the software, avoid downloading unauthorized software and staying vigilant over unsuspicious activity. According to a cyber security survey 67% of organizations say their employees lack basic cybersecurity awareness, up from 56% in 2023. By 2025, 75% of companies have made improving security culture a top initiative. To address this, companies should regularly conduct mock drills to bring awareness about the phishing activities and risks of clicking unknown links, visiting suspicious websites and opening corrupt files or attachments.
Take precautions while using RDP (Remote Desktop Protocol)
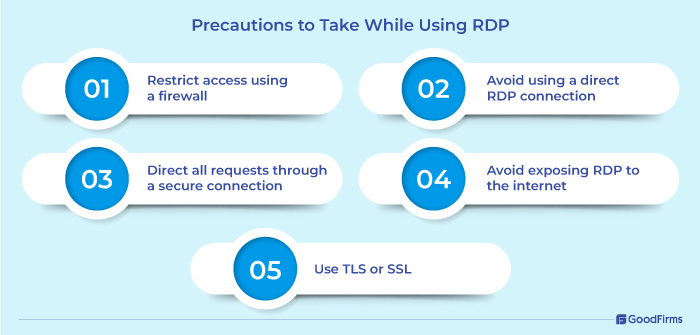
When someone uses RDP protocol to control a remote desktop, there is a risk of man-in-the-middle attacks. As a security best practice, users can implement a few steps like restricting access to RDP, avoiding using direct RDP connection and instead establishing RDP sessions through a Remote Desktop Gateway, directing all requests through a secure connection, avoid exposing RDP to the internet, and use TLS or SSL for secure communication.
Remove unused accounts
IT and security teams often fail to audit the active directory and let obsolete accounts go undetected. Hackers' access to such accounts can significantly risk the security of the remote desktop software. On the safer side, it is advisable to remove unused or inactive accounts from the remote desktop software.
Perform regular audit of remote desktop software
According to the 2025 UK Cyber Security Breaches Survey, only 31% of businesses carried out a cybersecurity risk assessment in the past year. Proactively monitoring or auditing the remote desktop software can significantly reduce the risk of software breach. Also, maintain a review logs with complete information about the remote desktop software access, such as request types, IP addresses, date/time, etc.
Implement strong security for remote sessions
Remote desktop software comes with various security settings and allows users to select options to strengthen their remote session security. Security measures such as two-factor authentication, strong passwords, permission-based access, avoiding public Wi-Fi to access remote sessions, etc., could also secure the remote sessions. Tools like Zoho Assist and Anyviewer come with session time-out features to keep remote desktop software safe. By enabling this feature, the system automatically logs out users from the session after a period of inactivity.
Future trends in remote desktop software security

Artificial Intelligence
The global AI in cybersecurity market grew from USD 25.4 billion in 2024 to an anticipated USD 31.4 billion in 2025, and is expected to maintain a strong 24.1% CAGR through 2034. AI will keep adding value to each and every industry and its applications in improving remote desktop software security are equally anticipated. AI, when embedded with remote desktop software can help detect anomalies in the network and raise alerts if unusual behavior is identified in the network. Likewise, AI can be used to continuously monitor the risks at the remote desktop endpoints and block any suspicious users trying to gain unauthorized access, regardless of their location. Remote desktop software can use AI to update security patches automatically and keep the system up to date. As AI technology becomes more advanced and intelligent, it can be used for biometric authentication to ensure that only legitimate people can access remote desktop software.
Integration of Remote Desktop Software with Advanced privileged management tools
Going forward, the remote desktop software will come interlaced with robust end-point privileged management and privileged password management tools to get better control over system security and manage all the business privileges. It will help to minimize the security threat that is caused due to poor management of permission access control.
Quantum computing
Another impressive piece of technology that could be groundbreaking in enhancing remote desktop security is Quantum Computing. Quantum Computing that generates QKD (Quantum Key Distribution) can be used to make authentication more secure and safe. QKD that relies on Qubits to create a shared secret key that is nearly impossible to intercept or replicate can be used for remote desktop authentication processes.
Blockchain
Blockchain technology is a great choice to secure remote desktop connections. Unlike traditional remote desktop software that uses a centralized server to store all the information in one place, the blockchain decentralized structure stores information within a network of nodes. This makes it almost impossible for hackers to steal the remote desktop users’ credentials. IT administrators also use Blockchain to track who accessed which files at what time to easily identify any unauthorized access to the system. In addition to that, Blockchain can also be used to secure the remote desktop endpoints by integrating blockchain with it. Some companies envision replacing password-based remote system access by combining SSL certificates with the blockchain. SSL certificates combined with blockchain confirm the authentication of the users without them entering the password.
Conclusion
Throughout the technological evolution, flexibility, convenience and finding the right solutions to adversities have remained the central focus for tech innovators. Undoubtedly, remote desktop tools have emerged as the most useful tech innovation for modern businesses in solving many of the core issues associated with organizational security, performance, team collaboration and data accessibility. The day is not far when remote desktop solutions, along with technologies like AI and blockchain, could make remote work more efficient, seamless and immersive than ever.
But like other tech gadgets or software, remote desktop tools are also prone to cyber threats by hackers to get unauthorized access to end-users' systems. Therefore, organizations need to rethink their remote access strategy and should thoroughly inspect their remote desktop systems for potential security vulnerabilities. There is a desperate need for IT professionals to implement the best security practices while staying in touch with the new technological trends to avoid cyber attacks on their remote systems.




.jpg)



