Remarkable IT support depends on several factors, and one such is undoubtedly using the right tool to gain secured remote access. While providing remote access is crucial in this day and age, it comes with its own set of challenges. Several organizations are implementing remote support software solutions to balance flexibility and security. Secured remote systems use a combination of policies, compliance, protocols, procedures, and technologies to safeguard the shared information - data in rest, data in use, and data in motion, and to prevent data breaches.
Unsecured remote access systems are prone to data breaches. “A breach alone is not a disaster, but mishandling it is,” says an expert.
As data breaches are getting sophisticated and disruptive, following a few best practices to mitigate the situation and to continue operation without any major impact is the need of the hour.
This blog tries to shed some light on the 13 best practices to handle data breaches in remote support. The blog also tries to answer a few common questions like;
- What is a data breach? What are its consequences?
- What are the different motives of the attackers behind data breaches?
- Why are data breaches common in remote support?
- How can AI prevent data breaches?
- What are the trends defining the future of secured remote support?
What is Data Breach? What are its Consequences?
A data breach refers to an incident, event or situation when confidential data of customers or businesses is exposed to entities that do not have access to it. A data breach can be intentionally caused by hackers and competitors or can be unintentionally caused due to technological upgrades. When hackers gain access to the private data of businesses, most of the time, they sell it to competitors, businesses, or anyone looking to purchase it, causing serious damage to brands, their customers, employees and other stakeholders. Not only this, but the hackers can also extort money from businesses to not sell it or make it public online.
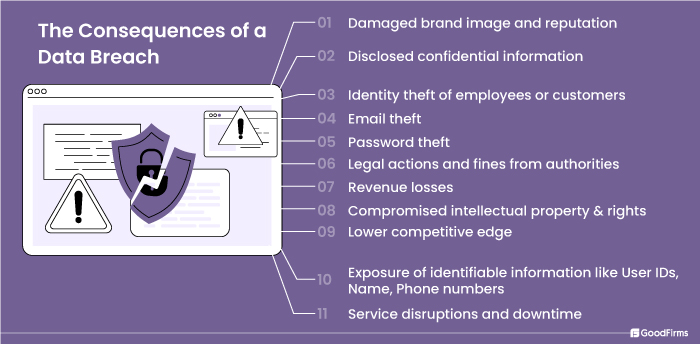
Data breaches can have serious impacts on businesses, and the stakeholders can expect financial and reputation damage. Businesses can also be subjected to non-compliance fines and legal implications from regulatory authorities, including the HIPPA, GDPR, PDPA, CCPA.
Reports indicate that the average cost of data breach is $4.45 million and in 2024, they are expected to cost the world a whopping $9.5 trillion, meaning huge loss in terms of profit and revenue. Businesses could face operational challenges due to intervention by legal authorities which often leads to service disruptions, and slowly a lower competitive edge. A data breach can also affect the employees if their personal data is publicly disclosed. The cases of identity theft in such situations are common that can seriously damage the reputation, career and personal lives of employees.
5 Top Motives Behind Data Breaches In Remote Support
Cyberattackers target business and confidential information for many purposes ranging from ideological differences and personal gains to money-making and social awareness. The main types of motives of cyber hackers are as follows;
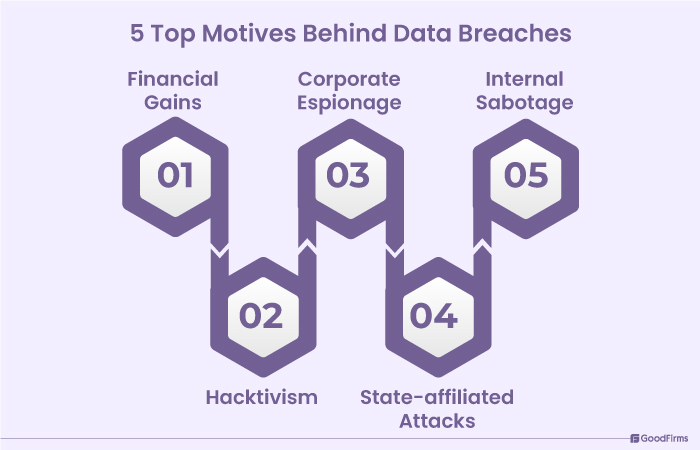
#1 Financial gains
Hackers with this type of motivation typically target organizations with huge data or money. Generally, the hackers are paid by other firms, particularly competitors, but many times, they can act individually to extort money. In October 2023, hackers demanded $200 million from Boeing to not publicly disclose 43 gigabytes of company data. In fact, 62% of financially motivated cyberattacks involve extortion. Ransomware attacks are common for extortion, which can be easily mitigated through patch management software.
#2 Hacktivism
Cyberattacks due to Ideological differences are common at the present time. Such attacks can also be referred to as hacktivism in which hackers target organizations that are perceived as evil, unethical or dangerous to society. These attacks are not motivated by financial gains rather the hackers use their skills and expertise for the profit of the society or for social causes. A recent example is the attack on the server of the Iranian judiciary by a hacktivist group named Edalat-e Ali. The attack was done to disclose the unethical acts of the Iranian government during the 2022 uprising and subsequent events to the world so that the government can be held accountable.
#3 Corporate espionage
When a business or entity steals confidential information of a business for commercial purposes or to gain a higher competitive edge, then the act is known as corporate espionage. Mainly, competitors are responsible for corporate espionage cases. For example, in 2023, Microsoft found a cyberhacking campaign against Taiwanese companies having unique techniques and technologies. The aim was to steal the stealth techniques and methods of these firms that can be reused to improve the broader industry visibility and business operations in other regions. Another significant example of corporate espionage is the fight between Apple and Rivos. Apple sued Rivos claiming to steal the company’s trade secrets. Apple alleged that Rivos hired several former Apple employees to steal their sophisticated system-on-chip technology. However, later on Apple settled the related claims.
#4 State-affiliated attacks
Governments, directly or indirectly, are involved in these attacks to benefit their nation or destabilize the infrastructure of other nations. Typical targets of these attacks are businesses and government organizations who are working in national interests. Attack on 22 Danish energy companies by a Russian state-affiliated group, i.e., SandWorm, is one of the major examples of state affiliated attacks. Recently, a leading Chinese contractor company, I-Soon was subjected to a data leak which revealed how the company was doing espionage work for the state. The company was involved in compromising multiple Hong Kong organizations, universities and NATO institutions.
#5 Internal sabotage
It refers to the events in which either working or soon-to-be-leaving employees are found involved in disclosing the data of their company to other parties or competitors. As per cyber risk research, the average cost of insider risk and incidents is around $16.2 million. And in an era when around 80% US workers are working in either hybrid or remote mode, the chances of internal sabotage by employees grow further. Intentionally or unintentionally, internal sabotage can be caused by any employees, partners, suppliers, and other stakeholders, so keeping an eye on all is advised.
One of the leading examples of unintentional internal sabotage is the Pegasus Airline data leak. Due to a misconfigured AWS cloud bucket by an employee, the flight details, staff information and source code of the company got publicly available on the web. Microsoft is another example of unintentional sabotage. Microsoft AI researchers accidentally uploaded 38 terabytes of private data to GitHub when publishing the storage bucket of open-source training data.
Besides these motives, many hackers and cyberattackers are also driven by the desire for recognition, revenge & vengeance, challenge, etc., prompting them to commit cyber crimes. Every business, irrespective of the industry and size should invest in cyber security tools such as Remote Desktop Software, Remote Work Software and Incident Management Software with advanced features and capabilities to prevent unauthorized access from hackers.
Why Data Breaches are Common in Remote Support?
Post-covid, businesses from almost all industries are widely using remote desktops and support systems. These systems require an active internet connection to establish RDP protocols between the server and the host, hence is a popular target for cyber attackers. Additionally, the support team and end users also need to remotely share files and documents, which can be targeted or modified by hackers through malware, ransomware, or phishing. As the IT team and server are located distantly, issues associated with cloud misconfigurations, unsecured networks, widened attack surface, DDoS attacks, unencrypted communication, unpatched tools, etc., can easily arise, resulting in vulnerable systems. Through these vulnerable systems, hackers get an easy entry point to access confidential business, employee, or customer data. Furthermore, the increase in BYOD - bring your own device work policy and lack of proper IT awareness among employees and consumers is also another reason behind the increased data breaches in remote support.
What are the Best Practices to Handle Data Breaches in Remote Support?
Here are the leading best practices that a business can implement to prevent data breaches during remote support;
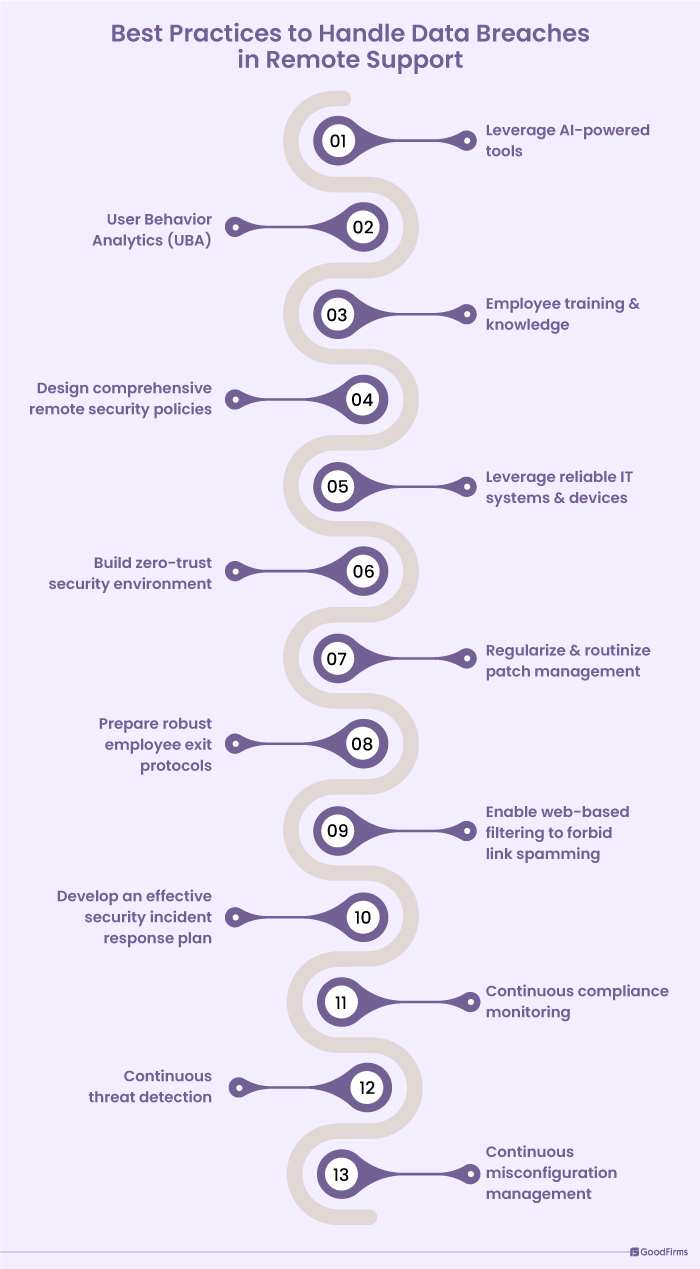
#1 Leverage AI-Powered Tools
Leveraging AI-powered remote support tools greatly helps businesses easily prevent and proactively handle the data breaches during remote connections. These tools leverage advanced AI models and algorithms that can analyze past and present cyber incidents and data to personalize the support, automate alerts and notifications, recommend best solutions, determine potential risky endpoints, deploy endpoint management assistants, provide real time insights, quickly identify root cause of the breach, respond to breaches, combat spam and phishing, identifying advanced malware, etc., within minutes. Selecting a reliable AI remote support software is critical to ensure optimum protection against the hybrid and ever evolving cyber threats. Majority of the businesses are opting for AI-powered tools to protect themselves against rising cyber threats. Interestingly, in April 2024, the Department of Homeland Security announced the formation of The Artificial Intelligence Safety and Security Board to support AI’s Responsible Development and Deployment, and for the security and resilience of the nation’s overall infrastructure by foreseeing the evolving threats.
#2 User Behavior Analytics (UBA)
It is a method used to analyze and track the behavior of users, machines and digital systems in order to detect any deviation from baseline behaviors regarding security anomalies and intrusion attempts. Implementing UBA systems is a great practice to prevent data breaches in remote support as it helps identify baseline behavior, demonstrate compliance, spot evidence that users have shared credentials, streamline threat workflow, review security and access logs and do many more things to ensure optimal security. For instance, UBA helped HealthEquity, a financial technology and business services company in the United States to identify anomalous behavior from a partner’s device. HealthEquity identified that a personal device of a business partner was compromised by a third party. The company promptly took action and isolated and triaged the issue so that it can’t impact the organizational data and privacy.
#3 Employee training and knowledge
Employee training and knowledge is always paramount when it comes to preventing cyber breaches. Without proper training and IT knowledge, employees often commit mistakes that hackers can leverage to get unauthorized access to the system. Regular training and development sessions associated with access management, data sharing, spam detection, etc., should be provided to employees regarding cyber incident management to reduce the chances of data breaches. Additionally, training to reject requests/information from unknown sources, use password managers, run regular updates, never leave devices unattended, create complex and strong passwords, avoid clicking on suspicious links, emails, etc., also benefits employees in ensuring better cybersecurity.
Not only employees but end users should also be made aware of IT risks and challenges so that they can protect themselves during remote support. A recent example of a cyberattack due to poor user knowledge is of Roku, an American technology company. Hackers got access to the stolen login credentials of Roku users which were used on other platforms, thereby impacting around 15,000 Roku's accounts. Another example is the data breach at ancestry service provider 23andMe that affected 6.9 million user profiles. Such breaches could have been avoided if users had proper knowledge of how to set an effective password.
Setting weak passwords, misusing personal email, information oversharing on social media, careless use of mobiles and collaboration tools, etc., are some of the major mistakes employees make due to poor IT knowledge, as indicated by Statista (Below-given Image).
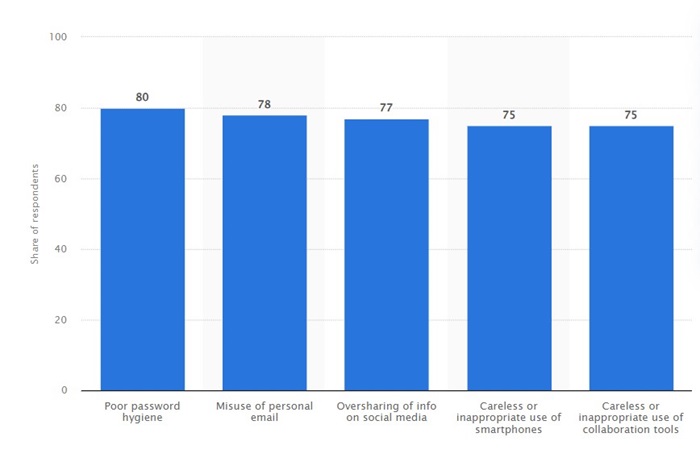
(Source: Statista)
#4 Design comprehensive remote security policies
With remote security policies, businesses can easily manage the cyber threats and issues during remote support. A comprehensive remote security policy clearly sets the importance of information security for organizations, specifies company’s obligations to data privacy and comply with industrial regulations. An effective remote security policy should define clear guidelines and instructions for USB connections, device control, access control, login/logout, reporting, password creation and sharing, data backup and restore, monitoring practices, file sharing, data privacy, network connections, screen sharing, etc., ensuring 360° protection.
Not only development, but the policies should be strictly enforced without any exceptions. Not properly following the policies can prove disastrous for any organization, as seen in IT services management company Okta's support case management system breach. The company failed to properly enforce the remote security policies and one Okta employee used the company-issued system to sign into the personal Gmail account, compromising the credentials of the customer support service account. Businesses should also enforce multi factor authentication to protect against unauthorized access. Data cloud company Snowflake is planning to enforce MFA for detecting and preventing unauthorized access after the company was hit by a significant data breach.
Businesses should enforce these policies on all the stakeholders, whether users, employees, partners, suppliers, or investors.
#5 Leverage reliable IT systems and devices
IT systems and digital devices are the backbone of modern organizations; hence, they should be carefully selected to ensure business continuity, maximum RoI, data protection, optimized downtime, and minimum cyber risks. For bringing better reliability to the IT systems and devices, businesses should properly invest in best-in-class firewalls, printers, premium VPNs, backup systems, remote desktops and support systems, antivirus programs, secure desktops and networks, anti-spyware, etc., for overall privacy and data security during remote support functions.
Zero-day attacks are the most common example of what happens in the absence of reliable IT systems and devices. In April 2024, a well-known cybersecurity company Palo Alto Networks detected a suspicious exfiltration attempt that was found leveraging a zero-day vulnerability with a weak firewall. Similarly, hackers exploited certain weak network storage devices of Kentucky-based Norton Healthcare, compromising the data of nearly 2,500,000 persons, which could have been avoided with reliable storage devices with advanced vulnerability management capabilities.
Reliable IT systems and devices also assist with business scalability as they integrate sophisticated components, system architecture, and maintenance practices. If existing systems are not reliable enough, they can be improved with reliability testing, modeling, engineering, and optimization.
#6 Build zero-trust Security environment
In this era of remote work software and environment, zero-trust models are emerging as a secure alternative to easily manage the distributed nature of digital tools and technologies in a risk-free way. Zero-trust security is a concept where any device/user/system, whether outside or inside the organization is allowed to gain access only after proper verification to ensure data safety and integrity. These include granting limited access, verifying every access request, micro-segmentation, continuous remote monitoring and management, dynamic trust evaluation, etc.
#7 Regularize and routinize patch management
Best patch management practices like routinizing and regularizing help users and employees better understand the organizational patch management process. Through this, they can eliminate any mistake in the patch update process. When employees lack proper knowledge regarding the organizational patch management procedures, then service downtime and performance issues are common. Businesses having global operations should necessarily have proper patch management and regularization policies in place, otherwise they can experience cases like Austin-based cybersecurity technology company CrowdStrike’s technical failure on July 19th, 2024. The company applied an ill timed patch update that led to the service disruptions for several industries including aviation, healthcare, IT, etc., on a critical week day like Friday. The service disruptions could have been avoided if CrowdStrike had worked on a proper patch management process and policy.
#8 Prepare robust employee exit protocols
Robust employee exit protocols are a must for organizations that don't want to compromise their data privacy and security during remote operations. Employee exit protocols typically deal with the laws and regulations that are created to safeguard organizational data when an employee resigns or is terminated due to various reasons. Employee exit protocols in this cyber era should focus on the following aspects;
- Implementing role/location-based access controls
- Revoke user access as soon as the employee resigns
- limiting employee access to critical data
- Update password
- Retrieve devices, if provided
A prominent example of intentional internal sabotage is the case of Tesla data breach. Two former Tesla employees caused a major data breach that disclosed information of around 75,735 present and ex employees of Tesla. The breach could have been avoided if Tesla followed strict employee exit protocols.
#9 Enable web-based filtering to forbid link spamming
Web-based filtering refers to the process of blocking specific websites and links that can be spam, offensive, inappropriate, etc., and may be used for hacking and cyberattacks during remote connections. Business email compromise (BEC) and phishing are the leading types of cyberattacks that involve clicking on unwanted or potentially dangerous links through spoofing an email account or website, sending spear-phishing emails, using malware, etc. Only reliable remote support software with DNS-based filtering options and AI features is the solution to these problems, which can restrict the user's access to web pages that have malicious links and provide better security against such attacks. Focus on reliable and strong SSL certificates can also help combat web-based cyber fraud. Majority of attacks such as bulk phishing, spear phishing, BEC, ransomware, smishing, vishing, social media attacks, etc., (as mentioned by Proofpoint in the below-given image) are caused through links, hence, a web-based filtering tool can help protect against such attacks.
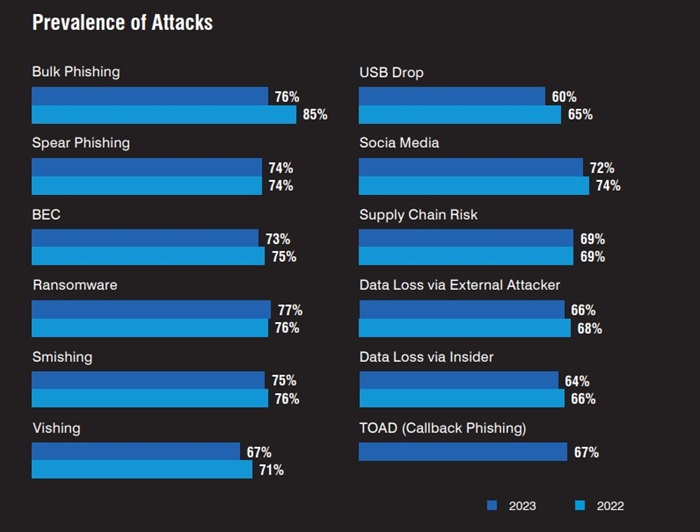
(Source: Proofpoint)
While small companies are easy targets for these types of attacks, they can also target bigger organizations like Uber. In 2022, an independent cybersecurity researcher found evidence of phishing attacks on internal systems of Uber in which internal screenshots of AWS, SentinelOne and Slack were leaked online by a group "vx-underground".
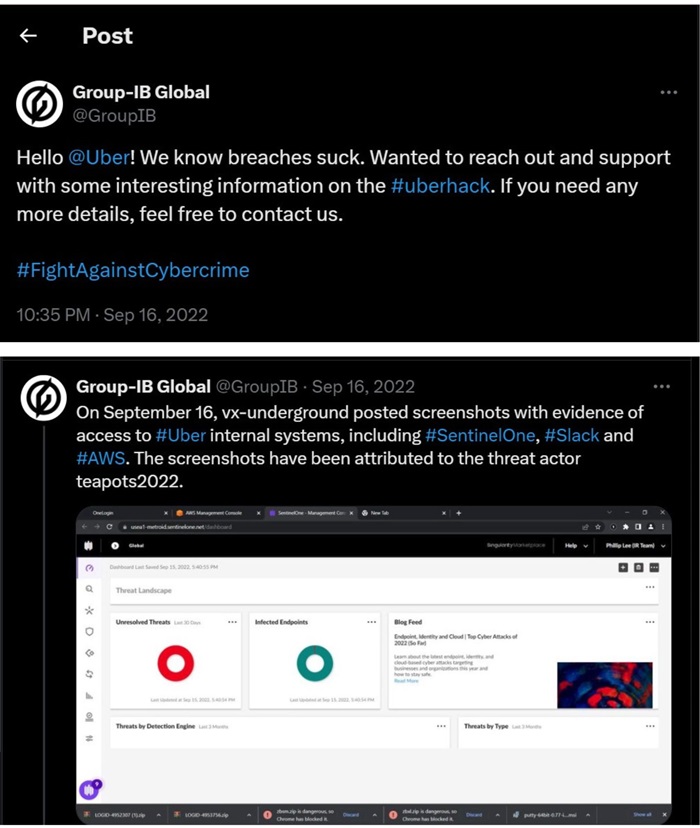
(Source: X)
In 2023, another leading UK based media house, The Guardian became victim to a phishing attempt owing to which the data and personal information of several UK staff members was illegally accessed by criminals.
#10 Develop an effective Security Incident Response Plan
A security incident response plan is a critical framework to quickly respond to and resolve cyber incidents upon happening, limiting damage to the system and business. It specifies the roles and responsibilities of vulnerability management to the employees and users in case of a data breach during remote support or connections. Even the industry regulators have set the limit of 72 hours for responding to breaches once they are detected. The stages of an effective incident response plan should include breach verification, assessment, containment, and post-breach response. Not only this, but the businesses should have a specific and separate team for incident response. Every member should have defined and clear procedures for identifying, containing, eradicating, testing and recovering from a breach.
#11 Continuous compliance monitoring
Continuous compliance monitoring is an important function of businesses and IT departments to ensure strict adherence with organizational policies, legal regulations and industry standards. Remote support tools with continuous compliance monitoring capabilities offer many features and tools to monitor network activity for anomalies, regularly review system logs for suspicious access attempts, prevent legal fines, build trust, maintain brand reputation, identify compliance risks and do many more related functions with ease to ensure every legal compliance has been met.
#12 Continuous threat detection
"There are only two different types of companies in the world: those that have been breached and know it and those that have been breached and don't know it." - Ted Schlein
With the increase in cyber crimes, the need for real-time threat detection during remote support sessions is also rapidly growing. Businesses are investing in remote support software with continuous real-time threat detection capabilities to detect and mitigate cyber breaches in a timely manner. It comes with log data monitoring, real time alerts, network traffic management and many more features to proactively protect against evolving threats.
#13 Continuous misconfiguration management
Cyberattacks due to cloud, database, and server misconfigurations are also becoming increasingly common. Such issues arise due to overly permissive access, unrestricted ports, storage access misconfigurations, under-configured systems, using default credentials, etc., which can be eliminated through remote support software with robust continuous misconfiguration management capabilities. Business giants like Toyota, Tesla, Alibaba, Pegasus Airlines, etc., have all been victims of cloud misconfigurations at some moment. A leading example is Toyota, in which cloud misconfigurations exposed data from 260,000 customers. In 2022, the Shanghai government summoned the Alibaba executives regarding a data breach caused by a misconfigured database.
Now that we are familiar with the best practices to handle data breaches in remote support, we need to also understand the role of the most promising technology - Artificial intelligence (AI) in the prevention of data breaches in remote support models. Here we go..
How Can AI Prevent Data Breaches in Remote Support?
“Artificial intelligence and generative AI may be the most important technology of any lifetime.” — Marc Benioff, Salesforce.
We all are aware of the latest news about the payments processor Visa’s investment in AI technology enabled the company to escape from the 80 million fraudulent transactions of $40 billion value. AI is undoubtedly playing an increasing role in cyber defense mechanisms ranging from task automation, data analysis to decision making and trend predictions. In fact, AI and LLM technologies are valuable tools to combat the fear of increased cyber risks due to Generative AI, as per 32% workforce.
Top Ways AI is Strengthening Cybersecurity include;
- Advanced threat protection
- Behavioral analysis
- Threat detection and response
- Malware analysis
- Phishing detection
- Security policy enforcement
- Security document analysis
- Security logs audits
- Resilience testing
Not only this, but AI remote support software can also learn from the past data and incidents to understand emerging cyber threats so that they can be prevented and eliminated before they impact the operations at a huge level.
Trends Defining the Future of Secured Remote Support
Here are some of the major trends that are anticipated to define the future of secure remote support as follows;
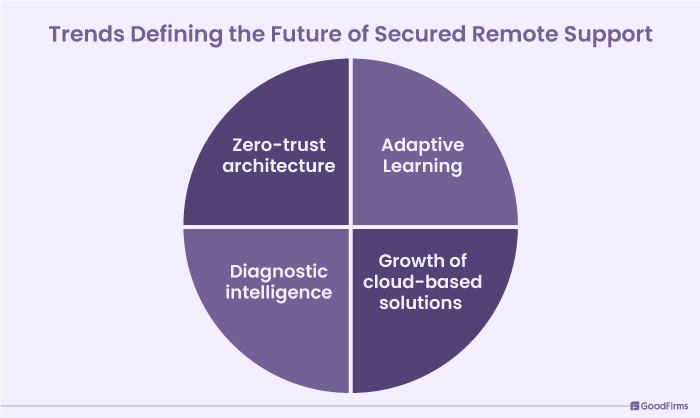
Adaptive learning
Emerging technologies like AI, ML, deep learning, etc., greatly improves the adaptive learning capabilities of remote support systems. As hackers keep developing new tools and technologies, the adaptive learning capabilities can be of great importance in staying ahead of the cybercriminals and strengthening the overall defense against ever changing cyber threats.
Growth of cloud-based solutions
While the security concerns of cloud solutions are still on the rise, cloud-based remote support software systems are still working to improve their security and configurations. Further advancements in the security, scalability, flexibility, and performance of these solutions are likely to increase their usage across the IT departments, delivering superior remote support.
Zero-trust architecture
The idea that nothing is secure enough to protect the organizational data and that every step should be taken to prevent the breach will be a major trend in the upcoming time. Remote support software tools with zero-trust architecture will offer proper account verification and authentication procedures to allow access to only verified users. Carrying out verification during each login, logout, file sharing, etc., is beneficial in data sharing between authorized persons only.
Diagnostic intelligence
This trend is also likely to improve the security of remote support software systems. Businesses will be able to see the state of devices and network on a real time basis, preventing any potential breakdown or system crashes. Remote support tools with diagnostic intelligence features could also offer self service for IT support, advanced endpoint protection and various other features to ensure timely response.
Conclusion
Intense data connectivity, network connectivity and operational connectivity is only going to lead to information breaches if proper measures are not taken. The above mentioned best practices to handle data breaches in remote support combined with advancing technologies like Blockchain and AI will eliminate critical challenges associated with unstable connections, data loss, identity theft, etc., propelling the security and performance of future remote support systems. Additionally, advancements in the remote support software with AI integration can act as a great investment by the users. Businesses can test the same by leveraging free and open-source remote support software, and then opt for premium software to gain unlimited preventional methods to handle data breaches in a remote support set-up.




.jpg)
