“AI will change cybersecurity—but so will the criminals using it.” Katie Moussouris, Founder & CEO, Luta Security
From not so important to one of the most sought after IT management components, cyber security has become a lifeline for the sustainability and smooth operations of modern businesses.
Cyberattacks are no longer treated as isolated disruptions owing to their severity levels. Increased use of hybrid infrastructure, remote working tools, automation platforms, and even AI has made the business landscape more connected, making businesses more prone to cyberattacks. The speed, scope and intensity of the cyberattacks have escalated today, and businesses need to go beyond their traditional approaches to ensure optimal cyber security capabilities. Investing in AI-powered cyber security software solutions will be a wise decision.
If you are looking to:
- Understand the risk
- Detect, investigate, and respond to threats
- Learn to mitigate and be secure
- Transform your security with AI-Powered Cybersecurity tools
Then, this blog will cover all about how Gen AI can embrace Gen AI cybersecurity. Here, Goodfirms has compiled several key cyber security trends that businesses can apply in 2026 and can benefit with a highly effective cyber security strategy. Also, the blog highlights a few tips on optimally leveraging these trends. The blog brings together industry-leading threat intelligence and best-in-class threat management with AI-powered cyber security solutions to detect, defend, and function without any disruption.
Key Cyber Security Challenges - What Businesses Should Know and Practice:
In 2026, the cyber security landscape is expected to become more complex. Hackers leveraging Artificial Intelligence and Machine Learning will become more mainstream, giving rise to new challenges for businesses.
In a latest survey, 47% businesses cited AI-powered cyber attacks as their top concern.
Alarmingly, 90% firms lack the maturity to defend against evolving AI-powered attacks. These attacks typically are carried out to exploit weak IT endpoints and vulnerabilities in business tools and AI systems.
“Not only has it become easier for hackers to launch targeted cyberattacks, but AI also enables them to scale their attempts at an unprecedented pace. Hackers can generate malware code en masse and automate attacks.” Naveen Balakrishnan, Managing Director at TD Securities
Therefore, it is critical for businesses to understand the ways through which technologies like AI are used to attack and defend threats. Here is a breakdown of the same;
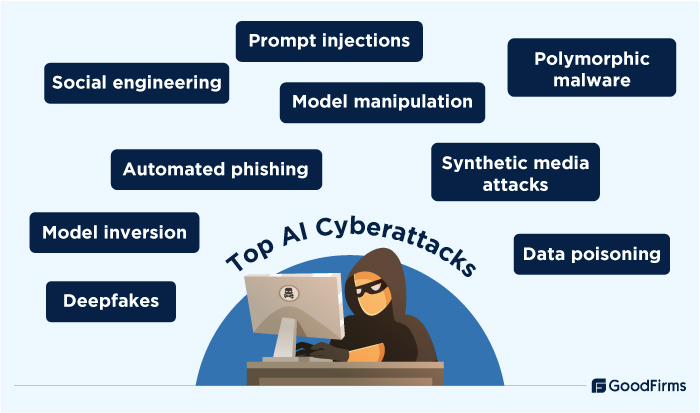
The top AI-driven Cyberthreats

Hackers will leverage Al to speed up, improve the scope and efficiency of the attack…
With the AI evolution, hackers are no longer confined to traditional attack strategies. Not just humans, now they are using trained models, AI agents, and sophisticated tools collectively to enhance the impact with little effort. Deepfakes, synthetic media attacks, prompt injections, model manipulation, data poisoning, automated phishing, model inversion, social engineering, polymorphic malware, etc., are a few top AI-powered cyberattacks that will become more common in 2026 and beyond.
AI-powered phishing
India reported major cyber scare due to AI phishing - 7 out of 10 organizations faced AI-based cyberattacks. 71% organizations have reported that they faced phishing attempts due to AI.
“AI fuels productivity while also heightening risk through insufficient governance and its expanding use in attacks. Managing information securely and intelligently is essential to building resilience in organisations of any size,” reported the executive VP of a global firm dealing with information management for AI.
Adaptive malware
Adaptive malware refers to the threat actors that can dynamically evolve and evade detection. Adaptive malware uses AI to dynamically generate malicious scripts, obfuscate their own code, and alter behavior mid execution. Recently, Google flagged an AI-powered adaptive malware that can constantly change itself and its attack tactics to prevent detection from antivirus programs.
AI-driven ransomware
According to the 2025 Ransomware report, nearly 48% organizations cite AI-powered ransomware attacks as one of the leading cybersecurity threats at the present time. In addition, 85% of businesses reported that traditional threat detection tools cannot prevent AI-powered ransomware attacks. India is witnessing a sharp rise in AI-powered ransomware attacks with nearly half of Indian firms experiencing at least one ransomware attack in the past year.
Autonomous AI agents
Google Cloud Cybersecurity Forecast warns about the rise of new AI agents that attackers can use to exploit crypto, cloud, and virtualization blind spots. The number of hackers leveraging autonomous AI agents powered by Agentic AI is rapidly growing. Earlier, the average time to exfiltration used to be 2 days. However, a simulation by Unit 42 of Palo Alto Networks on Agentic AI indicated that AI can help hackers execute their attacks completely under 25 minutes, meaning 100 times more speed.
Attacks targeting AI systems
The new Whisper Leak vulnerability exposes user prompts from popular AI agents to attackers, even within end-to-end encrypted traffic.
Cybersecurity experts have warned that AI agents pose serious cybersecurity risks. Additionally, ChatGPT vulnerabilities trick AI to leak data.
By 2028, around 25% of the enterprise cyberattacks will be caused by abusing AI tools involving both internal and external actors.
Anthropic, the parent organization of Claude AI, also recently disclosed that Claude is misused by attackers multiple times despite having strict security procedures in place.
AI-Powered Cyberattack Defence: How Can AI Fight AI-Driven Threats

To protect against these AI-powered cyberattacks, businesses need to restructure their AI-strategies, processes, people, and technology in a manner that allows them to outperform hackers. Some of the ways to actively protect against AI-powered cyber attacks are as follows;
- Investing in upskilling the IT expertise and adaptability of employees.
- Strengthening the governance.
- Strengthening human verification across critical workflows.
- Implementing strict data classification and access control capabilities.
- Leveraging secure communication and authentication channels.
- Performing digital footprint audits regularly.
- Investing in cloud security, network protection and backup technologies.
- Using AI-powered cyber security solutions.
- Sharing responsibility across digital environments.
While there is a rush to integrate AI into every system, businesses fail to add security. Hackers are increasingly and rapidly leveraging AI to attack their victims, a significant number of businesses are yet to integrate AI in their cybersecurity. As per the Threat Intelligence Report 2025, only 24% businesses have broadly integrated AI into multiple threat intelligence processes. AI-driven defense systems could be proved an indispensable choice owing to features like predictive analytics, automated response workflows, behavioral anomaly detection, etc. There is a strict need for businesses to understand the top ways AI is strengthening cybersecurity. These tools, when combined with the latest trends and best practices, can exceptionally improve the overall cyber security against evolving threats powered with AI.
Mastering the Fundamentals of Cyber security in 2026
While AI-powered cyber security tools and defense mechanisms can prevent a huge number of attacks, many still go unnoticed due to human errors. As per the Voice of the CISO report, 74% CISOs stated that human error is their top cyber security risk. This happens when IT professionals and businesses fail to understand and execute the basic fundamentals. Businesses should have a proper understanding of what’s in their control and what is not to effectively protect themselves against evolving cyber threats.
In 2026, Businesses should invest in Al governance…
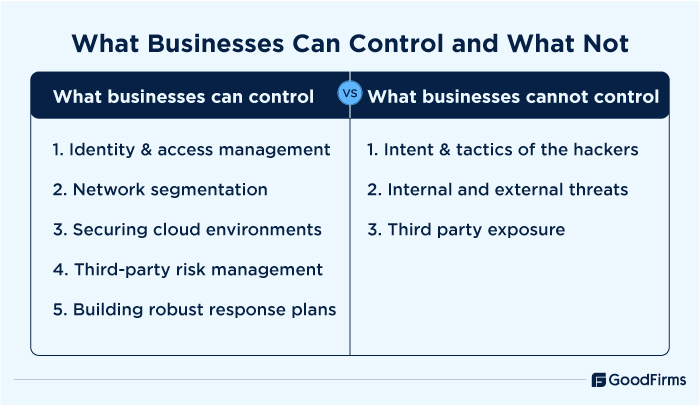
What Can Businesses Control?
Cyber security aspects like identity management, patch management, access management, network segmentation, network monitoring, CMDB, third-party risk management, response plans development, etc., can be easily controlled and managed by cyber security professionals securing cloud environments.
Additionally, they can secure their cloud posture through Cloud Security Posture Management and Cloud Workload Protection platforms that help actively prevent any accidental exposure of data and also protect against cyber threats.
Another factor that can be implemented is building robust response plans that outline how the organization can detect, contain, and recover from cyber incidents with defined roles, escalation paths, and timelines.
What Businesses Cannot Control:
While businesses cannot stop hackers from innovating new ways for cyber attackers, staying aware of the latest developments can help businesses anticipate and respond to cyber risks. Cyber security admins can subscribe to intelligence feeds such as CERT-In, CISA, and ISACs, monitor cyber security chatters, and use AI-powered proactive cyber security tools.
Additionally, these modern cyber security software solutions offer continuous threat exposure management, penetration testing, automated patch management, etc., to proactively identify and eliminate cyber vulnerabilities.
Top Cyber Security Trends For 2026
The top cyber security trends for 2026 are as follows;

#1 Agentic AI-powered defense for AI cyberthreats
Agentic AI-based cyber defense will become one of the most prominent cyber security trends in 2026. These systems can autonomously detect, respond, and mitigate cyber threats in real time, providing a more dynamic defense mechanism to protect organizational data and assets. Autonomous triage, playbook authoring, hypothesis testing, etc., are a few features of Agentic AI in cyber security.
These systems can continuously monitor network traffic, predict potential vulnerabilities, offer end-to-end alert investigation, automate remediation, and identify suspicious patterns, ensuring active protection against evolving cyber threats such as memory poisoning attacks, cascading hallucination attacks, goal manipulation, etc.
Due to increased use, the Agentic AI in Cyber security Market is expected to cross USD 1.83 billion in 2025.
For instance, Lowe’s, one of the largest hardware chains in the US, needed a scalable cyber security solution to enhance detection accuracy and automate remediation. For this, they implemented an Agentic AI-powered cyber security solutions that can investigate alerts up to 68% faster than traditional ones. Through this implementation, the company achieved a whopping 88% reduction in alert noise and 70% better threat response.
Top Tips to Ensure Maximum Security From Agentic AI
- Let AI agents triage, summarize, and suggest actions, but ensure containment requires approval from human analysts.
- Perform regular security audits and penetration testing to identify vulnerabilities in AI systems.
- Use anti-spam systems
- Use validation frameworks and code sanitization for both content fetched by the agent and user inputs.
- Implement fail-safe responses
- Ensure real-time monitoring of AI agents to detect unusual activities.
#2 Preemptive Cybersecurity
Preemptive cybersecurity is the process of proactively identifying and responding to cyber threats using AI and ML before their launch. In fact, by 2028, preemptive cybersecurity technologies will account for over 50% of the total IT security spending, as per a Gartner study.
These technologies leverage AI, predictive analytics, continuous validation, automation, red teaming, etc., to sense unusual network behavior, novel AI agent activities, weak signals, identity drift, and various other suspicious patterns, allowing IT teams to proactively predict hacker behavior, map exposure before exploitation, and eliminate any potential risks involved with the IT infrastructure.
Organizations can save up to $1.9 million in cybersecurity costs through AI and automation.
For instance, Microsoft’s models that process over 100 trillion security signals block over 4.5 million malware files on a daily basis, before they impact the IT systems of its users, partners, and other stakeholders.
Some tips to optimally implement preemptive cybersecurity are as follows;
- Implement autonomous red teaming tools to simulate potential attacks.
- Integrate threat forecasting abilities through AI-based trend mapping and pattern analysis.
- Optimize existing real time tracking and reporting metrics with more accurate ones.
- Continuously validate and improve the cyber defenses.
#3 AI-powered deepfake detection
Another top cyber security trend in 2026 is AI-powered deepfake detection. It is becoming a serious concern that involves the creation of hoax videos, images, and sound.
25.9% of business executives have experienced at least one deepfake incident that targeted their financial or accounting data, mentioned a study.
BEC, vendor fraud, KYC evasion, brand abuse, etc., are a few AI-powered deepfake methods.
From the deepfake case scam of Elon Musk endorsing a radical investment opportunity to hackers impersonating a senior official of a British engineering company, deepfake cases have been on the rise lately.
Cyber security tools with AI-powered deepfake detection capabilities are crucial in such times to prevent deepfake deceptions. These tools can analyze media for subtle inconsistencies such as pixel-level synthetic imperfections, inter-frame continuity issues, border compositing artifacts, facial anomalies, etc. Once manipulated content is detected, these tools instantly alert the IT teams to avoid it.
A few tips to effectively detect AI-powered deepfakes are as follows;
- Use methods such as media forensics, fakeCatcher-style signals, C2PA, etc., for high risk transactions.
- Setting clear policies and checks for money movement irrespective of meeting face.
- Capture data from attacks to improve SIEM detections and filters
- Implement face detection with integrated on-device deepfake protection
- Quarantine suspicious media to automated sandboxes for forensic scoring.
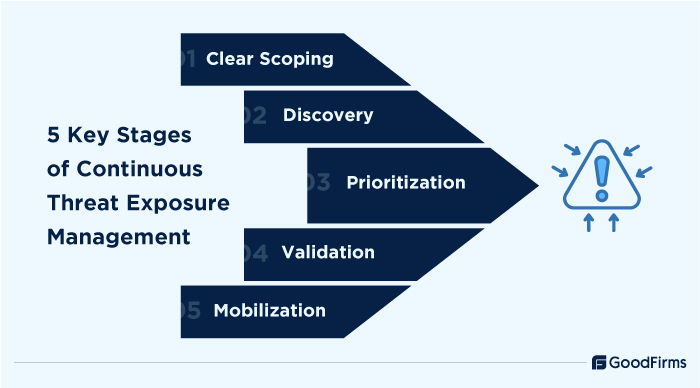
#4 Increased Adoption of Continuous Threat Exposure Management (CTEM)
Around 61% security leaders believe that their organization is failing to effectively identify and remediate exposure in hybrid environments, according to the Threat Exposure Validation Impact Report 2025. Continuous threat exposure management, coined by Gartner, can help businesses in continuously discovering, assessing, validating, and remediating exposure across hybrid IT environments. It offers continuous visibility, reporting, and remediation guidance that goes beyond vulnerability scanning to prevent and cut breaches. Through CTEM, businesses can mobilize fixes for a wide range of exposures, such as CVEs, configs, SaaS, cloud, etc.
For instance, Oman Arab Bank, a prominent financial institution in Oman, needed ongoing automated monitoring, risk-based prioritization, and a holistic view of its existing infrastructure. They implemented a CTEM platform that helped them achieve 40% faster remediation cycle, and 100% asset coverage within 90 days.
A few tips to better implement CTEM are as follows;
- Implement multiple threat intelligence feeds into CTEM process
- Keep the backlog small by autoremediating low blast radius misconfigurations
- Use exercises such as breach and attack and purple-team exercises to continuously validate the decisions.
#5 Quantum Security
With the rise of Quantum Computing, Quantum security will become one of the leading cyber security trends in 2026. In fact, researchers from University of Kent raised concerns about the vulnerability of Blockchain and Crypto to quantum computing. With the constant rise in “harvest now, decrypt later”, businesses should focus on implementing post quantum cryptography standards, such as the one finalized by US-based NIST in 2024. Quantum security focuses on inventorying crypto, planning migration to NIST PQC, and adding crypto agility. Nearly 62% businesses are worried about quantum breaking today’s encryptions, yet only 5% have a defined strategy in place to combat it.
Tips for Quantum Security are as follows;
- Build a crypto bill of materials by identifying RSA usage, the lifespan of protected data, and third-party dependencies.
- Migrate backups, archives, and regulated data sets first that are most exposed.
- Mandate FIPS-approved PQC support from 2026
- Continuously track and monitor the implementation and migration process.
#6 AI-powered Zero Trust Security
“We in cybersecurity are all walking down the road together – and the world is constantly changing around us – and you must change your strategy accordingly. So, what is next in changing that strategy is to weave AI into each pillar of Zero Trust.” Michael Baker, Global CISO DXC Technology
Zero Trust security works on the principle “never trust, always verify” that involves continuous validation of devices, users, and data for every request made. It is rapidly becoming the default strategy across enterprises to ensure proper defense against cyber threats. Owing to this, the Zero Trust Security Market is expected to cross $88.78 billion by 2030.
Cyber security solutions with advanced AI-powered zero trust capabilities come with risk adaptive access, device trust inference, micro segmentation policy generation, conditional access, etc., features to prevent unauthorized access in real time. This is the right time for companies to ditch VPNs and embrace Zero Trust Security.
Giants like Microsoft shifted to zero trust security years ago, yet they expect that it will take a few more years for them to completely achieve their goals.
Here are a few tips to optimally leverage zero trust security;
- Implement strict phishing-resistant MFA and access control features
- Micro segment each and every app and data point as per priority
- Use a robust cyber security tool with advanced fraud detection, password management, and firewall capabilities.
#7 Security governance & compliance
Security governance and compliance will be among the top cyber security trends in 2026. Shadow AI, i.e., unsanctioned AI tools that are used by the workforce without proper governance and compliance, will become more common than ever. Additionally, new regional laws and standards such as NIS2, DORA, NIST Cybersecurity Framework, CISA, HIPAA, GLBA, etc., demand more transparency, tighter oversight, and faster incident reporting. Businesses are required to make changes to their existing processes, structures, and culture at multiple levels to ensure complete security governance and compliance.
In 2026, focusing on governance is beneficial for businesses in ensuring that they are structurally prepared for cyber incidents, while focusing on compliance helps businesses stay legally safe from penalties and fines.
Leveraging advanced cyber security software with below mentioned tips can help businesses strengthen security governance and compliance in 2026;
- Create and regularly refine governance frameworks with auto updating policies and dedicated committees.
- Map and maintain compliance inventory and tracker with name, status, gaps, roadmaps, etc.
- Implement reporting mechanisms for relevant metrics and KPIs.
- Automate continuous control monitoring and regular auditing.
#8 Emergence of Identity Exposure Management
Identity Exposure Management is another leading cyber security trend in 2026 that will help businesses strengthen their security against identity-based threats. In fact, identity-based threats account for 30% of the total intrusions, as per the IBM X-Force 2025 Threat Intelligence Index. In the first half of 2025 alone, identity-based attacks rose by 32%, according to the Microsoft Digital Defense Report. Identity exposure management focuses on who has what access, why, and how that access enables attack paths.
At times when non-human identities like API keys, automated agents, and service accounts are ignored by traditional identity controls, businesses should upgrade to modern cyber security tools with AI-powered identity exposure management that can account for each and every identity and prevent identity chaining.
Here are some tips for proper identity exposure management in 2026;
- Build an enterprise identity graph by inventorying every human and digital identity.
- Automate revocation of unused accounts and schedule quarterly access certifications.
- Simulate identity attack paths using breach-and-attack simulation and close them.
Conclusion - New Security Rules for 2026
With the integration of AI, cyber security is ushering into a new world; one that will be defined by proactive resilience, adaptability, and cyber intelligence capabilities. As a result, the global cyber security market is expected to reach $108.96 billion by 2030 with a CAGR of 10.8%. One of the major drivers behind this excessive growth is the rising demand to identify and eliminate AI-powered attacks. Amidst these AI attacks, static protection through simple-to-breach strategies is not sufficient; rather, businesses need proactive resilience, continuous monitoring of exposures, and real-time adjustments. This is possible by leveraging AI in combination with strong security frameworks that can learn, predict, self-heal, and improve with every breach. AI’s role is there as both attacker and defender.




.jpg)



