This is not another boring blog on remote desktop protocol…
Post-COVID, several companies have extended the facility and the freedom to work from any location, to access and manage machines from anywhere, ensuring security, productivity, and efficiency in the fastest and most affordable way via remote desktop solutions and application programming interfaces. Remote desktop access for IT and other business teams comes with several benefits, such as accessing systems, connecting, viewing files, running programs, sharing screens, maintaining systems, software, mobile support, and much more from any PC, Mac, iOS, and Android devices. Although the advantages are enormous, security-related challenges of remote desktop access for organizations and businesses are a matter of worry.
As businesses and individuals are increasingly relying on these solutions, ensuring data safety, security, and integrity is also equally crucial.
These security vulnerabilities in remote desktop protocols often emerge from weak protocols, poor configurations, human errors, etc., that can potentially damage the revenue and reputation of businesses. However, implementing a reliable remote desktop software with advanced security features and AI capabilities can get rid of these security vulnerabilities in remote desktop protocol (RDP), enabling remote teams to stay vigilant and mitigate the vulnerabilities whenever they arise.
This blog exactly tries to shed light on the top 10 popular remote desktop security vulnerabilities that a business should be aware of while establishing and running a remote desktop protocol. Readers will also be prompted about how dangerous they are…exactly how dangerous.
The blog will also highlight the future trends of remote desktop.
What are Remote Desktop Security Vulnerabilities?
Remote desktop security vulnerabilities refer to the weak spots, gaps, and security lapses that can provide unauthorized access to hackers and cyber attackers when establishing or running a remote desktop protocol. These vulnerabilities can be caused because of various reasons including weak user authentication, Remote Code Execution (RCE), and port targeting, incorrect implementation, misconfigurations, mismanagement, technical flaws, careless usage, etc. When identified by cyberattackers, these security glitches or vulnerabilities can be used for malware deployment, system control, data breach, etc., compromising the data integrity, performance, reputation, and sustainability of any successful business.
Why Are Remote Desktop Security Vulnerabilities Constantly Rising?
With the immense rise of hybrid and remote working, remote support, and remote monitoring & management (RMM), and remote desktop solutions have gained tremendous popularity. While remote desktop tools provide flexibility and convenience, it also has been an attractive target for cyber attacks. According to Sophos incident response report, out of the 90% of cyber attacks, hackers abused the remote desktop protocol to gain remote access to business systems. The growing reliance on remote desktop solutions across almost all industries has further amplified the cyber security risks that come with these solutions.
Currently, a large majority of the businesses and independent users leverage different tools, software, and ports to operate that are prone to the cyberthreats and attacks caused due to weak spots. Security is one of the top big concerns of remote desktop.
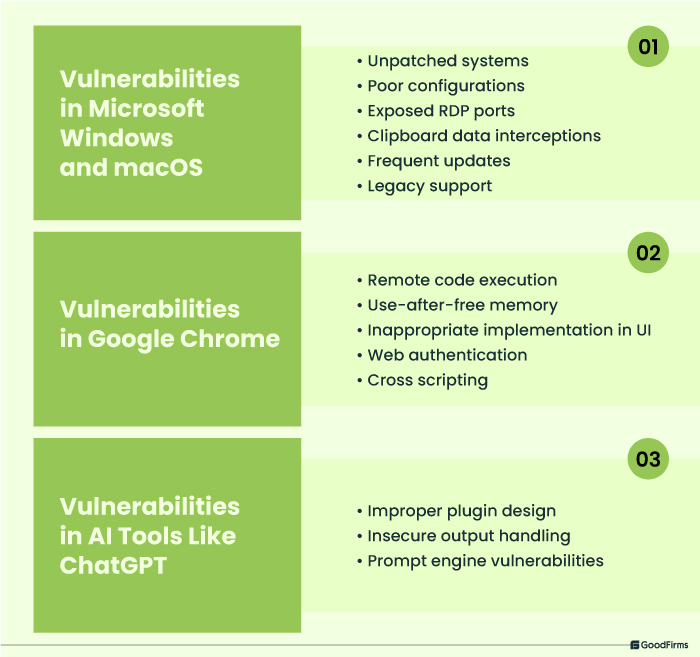
Microsoft Windows and macOS are the most used systems across the globe and have been also a reliable choice for establishing remote desktop protocols. Vulnerabilities like unpatched systems, poor configurations, exposed RDP ports, clipboard data interceptions, etc., can significantly affect the data security of these systems and the businesses using these systems.
Similarly, Google Chrome, which is widely used for browsing the web, has many times been targeted by hackers to gain illegal access to a user’s system. Use-after-free memory, inappropriate implementation in UI, web authentication, and many more Chrome-related vulnerabilities are there that directly affect the data security and safety of Chrome users.
AI tools like ChatGPT, Google Gemini, Microsoft CoPilot, and various other extensions, plugins, etc., are widely used by millions of people owing to which they are also vulnerable to cyberthreats. These AI tools, plugins and extensions can be a victim of improper plugin design, insecure output handling, prompt engine vulnerabilities, etc., that can cause serious issues to the functioning, reputation and performance.
Hackers continuously keep scanning the systems for vulnerabilities and when identified, leverage the security gaps through the use of automated tools, brute force attacks, AI-powered systems, Zero-day exploits, etc. The hackers even use advanced technological devices and systems that are built to jailbreak secure devices and bypass normal access controls.
The weaknesses or vulnerabilities in digital tools and software like Windows, Chrome, macOS, ChatGPT, etc., can only be eliminated through the implementation of proper cybersecurity practices and measures like regularly applying patches, enabling multi-factor authentication, disabling unused ports, leveraging browser isolation, applying strict content filtering, and using secure digital solutions that offer enhanced cybersecurity and data integrity.
10 Top Remote Desktop Security Vulnerabilities You Should Worry About in 2025
Intruders need an opening, an entry point, and that’s the beginning of destruction. Below, we share the most vulnerable elements of remote desktop security and strategies for mitigating them.
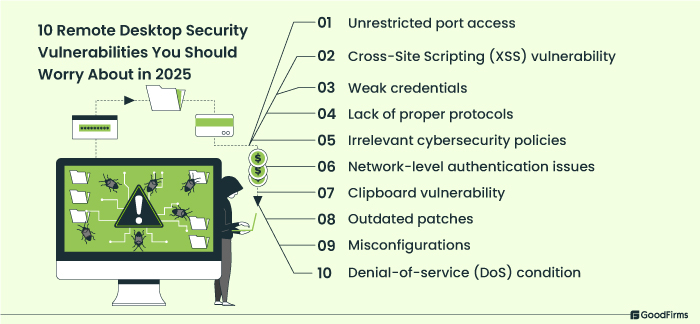
#1 Unrestricted port access
Situation: Ports are the doorway through which the network traffic flows, and access are granted. The ports are managed by the administrators. Typically, 3389 is the default port for remote desktop access for Windows-based systems. If left open without proper measures, this port can be used by hackers to gain unauthorized access to the IT systems. Hackers and cyber attackers can scan networks to find ports with unrestricted access to launch brute force, ransomware deployment, man-in-the-middle attacks, and other attacks to get access to vulnerable systems.
Remedy: To prevent unrestricted port access, the ideal solution is to use encrypted ports, usage of virtual private network (VPN) to restrict external traffic, implementing multi-layered security, configuring firewalls to limit exposure to the systems, patching, and leveraging port scanning tools, and cybersecurity software to continuously monitor and detect hackers trying to gain access from vulnerable ports.
#2 Cross-Site Scripting (XSS) Vulnerability
Situation: Cross-site scripting vulnerability allows intruders to run malicious Javascript in the victim’s computers that can compromise session data, credentials, or even full access to a remote desktop session. Through XSS vulnerability, cyberhackers can steal session cookies, impersonate users, and deploy sophisticated attacks like ransomware or lateral movement.
Remedy: In most cases, cross-site scripting attacks are carried out through a web-based gateway, so securing it with relevant and appropriate web application firewalls is crucial. Additionally, proper review of content security policies, implementation of strong input validation, use of modern frameworks, and tools that are secure by design, employing secure session management practices, and regularly focusing on the latest software patches and updates can also help identify and eliminate any cross-site scripting vulnerability.
#3 Weak credentials
Situation: Stealing credentials, and brute forcing weak passwords are also a major issue that one should worry about when establishing remote desktop sessions. Many users set weak passwords, which they even use during remote sessions. These weak security credentials when used during remote desktop protocols can leave the access open for cyber attackers. Hackers primarily use techniques like brute force attacks, keyword stuffing, automated tools, IP rotation, low-and-slow attacks, etc., to guess usernames and passwords.
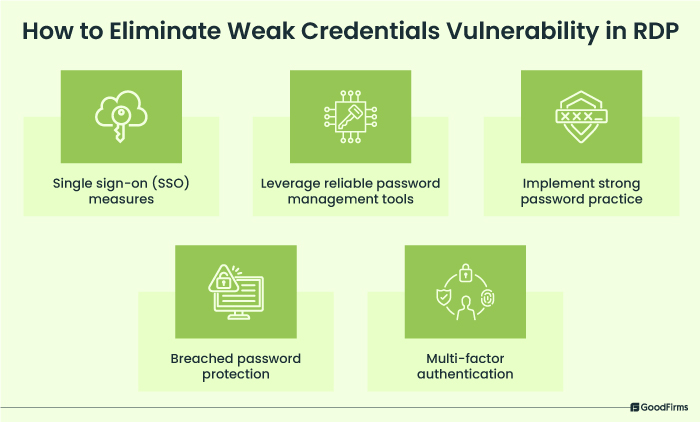
Remedy: To tackle weak credentials vulnerabilities, businesses and IT teams should rely on single sign-on (SSO) measures, password management tools, strong password suggestions, breached password protection, and multi-factor authentication to enforce strong password policies. Additionally, training should be provided to the employees so that they can set highly secured passwords and credentials, instead of relying on default credentials.
#4 Lack of proper protocols
Situation: Absence of the required protocols can lead to misconfigurations, insufficient monitoring, weak authentication mechanisms, etc., that allows hackers to gain unauthorized entry to the business and IT systems. At present, security protocols like TLS and SSL are essential to comply with legal regulations like PCI-DSS and HIPAA and prevent hackers from exploiting the vulnerable endpoints. When businesses lack these proper security protocols and measures during remote desktop connections, it can expose the sensitive business data to cyberattacks.
Remedy: To prevent cyberthreats caused due to lack of proper protocols, employees should be provided with proper knowledge and training to establish clear protocols. This helps them ensure comprehensive monitoring and logging to detect unauthorized attempts and activities. Addressing this proactively is essential as remote work continues to stay in the modern business landscape.
#5 Irrelevant cybersecurity policies
Situation: Another major vulnerability that can cause data theft during remote connection is irrelevant cybersecurity policies in place. Outdated and irrelevant cybersecurity policies can lead to gaps in security measures, meaning failure to address the current threats effectively. In most cases, irrelevant cybersecurity policies are created by employees who are not aware of the latest policies and best practices required to safeguard remote connections.
Remedy: Designing comprehensive remote security policies is among the best practices to handle data breaches in remote protocols. The best way to create comprehensive cybersecurity policies is to analyze the trend, research policies, educate employees and follow the best practices for data safety and integrity. Additionally, businesses should involve different departments in the policy making so as to ensure comprehensive coverage of all known vulnerabilities in the overall policy development. Businesses can also use advanced remote desktop solutions with detailed insights and data to create meaningful, relevant and up to date cyber security policies aimed at handling the complex evolving threats.
#6 Network-level authentication issues
Situation: Network level authentication (NLA) is a security feature that adds an extra layer of security when establishing remote connections. Issues with network level authentication can help hackers disable or bypass the network level authentication allowing them to access the critical business data. For instance, whenever a RDP connection is temporarily disconnected, it attempts to connect again. At this point, hackers can introduce unexpected network activity which would trigger the vulnerability and hackers can access any of the affected sessions.
Remedy: To prevent vulnerabilities caused by NLA, businesses should focus on strengthening their credentials policies, avoiding downgrading, disabling fallback mechanisms, leveraging highly secure password managers, and performing penetration testing methods to prevent problems associated with NLA. In addition, businesses and IT administrators can also rely on Network Mapping Software, Network Monitoring Software, and Network Security Software to prevent NLA related vulnerabilities.
#7 Clipboard Vulnerability
Situation: While clipboards are a valuable feature for streamlining workflows, they also pose a major security risk during the remote desktop protocols. This vulnerability was recently identified in CVE-2024-38131. When clipboard data is shared between a host and a client during an RDP connection, the Clipboard Virtual Channel Extension is vulnerable to hijacks like path traversal attacks and arbitrary code execution. With minimal interaction, attackers can inject malicious code into the shared clipboard data, gaining illegal access to the data copied by the users. Not only the copied data, but hackers can also gain access to the entire IT infrastructure, compromising overall business data.
Remedy: To eliminate clipboard vulnerability in remote desktop connections, IT systems should disable clipboard sharing when it’s not necessary. Additionally, only using advanced remote desktop systems with strong clipboard data security and clipboard activity monitoring capabilities can automatically prevent attackers from leveraging this vulnerability. Apart from these, regularly installing the latest Windows security updates is also pivotal to ensure complete data security and integrity.
#8 Outdated patches
Situation: In patch management, IT administrators identify and apply the latest security updates or patches to the business systems like software, application and other digital tools. When the patch management process is not carried out on a regular basis, software and applications may become outdated and hence, they become prime targets for hackers. For instance, CVE-2023-35332 vulnerability is leveraged by hackers due to outdated RFC 8996 protocol. Such types of cyber threats can be easily eliminated through an automated patch management system.
Remedy: An automated patch management solution can regularly identify and fix unpatched systems, perform comprehensive audits, and 24*7 monitor and test the endpoints, ensuring complete IT security during remote desktop connections. There are several benefits and best practices for the patch management that businesses should stay aware of for best results and optimal endpoint protection.
#9 Misconfigurations
Situation: Many of the times, issues associated with misconfigurations and incorrect implementation of RDP systems also result in security vulnerabilities. Misconfigurations and incorrect implementation can lead to major security lapses like failure to limit user permissions, allowing connections from every IP, etc.
Using default configurations can also make systems vulnerable, as hackers can exploit the default configurations to target the victim’s system.
Remedy: Such vulnerabilities can be only eliminated through proper CMDB tools that are designed to strictly enforce standard configurations across all systems. Additionally, access control lists can also be implemented to restrict access based on user roles. Besides these measures, IT teams should also conduct regular configuration reviews against the best industry practices and compliances.
#10 Denial-of-service (DoS) condition
Situation: In Denial-of-service (DoS), attackers overwhelm the server with a lot of requests aimed at disrupting the services intended for end users. As a result, users fail to access the remote desktop. In 2023, the DoS attacks saw a massive increase of 112% when compared to 2022. Most common methods for DoS attacks are SYN floods, UDP floods, volumetric attacks, smurf attacks. Lack of intrusion detection systems and unpatched systems are the main cause behind RDP-based DoS attacks.
Remedy: To avoid DoS vulnerabilities, businesses should use highly secured firewalls and intrusion detection systems. These can monitor the incoming traffic requests and block high volume or suspicious traffic patterns, designed to overwhelm the entire system.
Quick and Easy Tips to Eliminate Remote Desktop Security Vulnerabilities in 2025
With advancing technologies, hackers have also become more sophisticated in exploiting cyber vulnerabilities like unrestricted port access, misconfiguration, irrelevant security protocols, weak credentials, improper patch management, etc. This is very common with remote desktop connections. To get 360 protection against these vulnerabilities, businesses should deploy reliable remote desktop software with advanced AI-based security features like regular security audits, multi-layered security, strict access controls, secure clipboard data sharing, dynamic port management, automated patch management, etc. These features and capabilities can proactively protect the remote sessions against advanced and emerging cyber threats, DoS attacks, brute force attacks, etc., enabling a comprehensive approach to security during remote desktop connections.
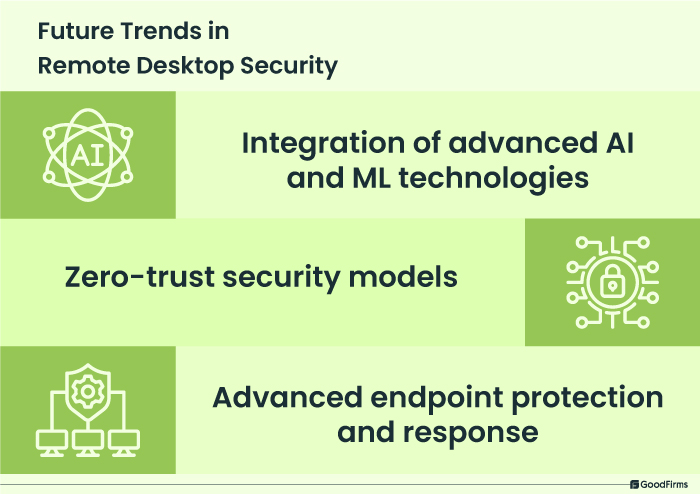
Future Trends in Remote Desktop Security
In the near future, RDP could see significant advancements in encryption algorithms, authentication methods, and intrusion detection systems. Advancement in technologies like AI and ML, endpoint protection, zero-trust security models, etc., will help IT administrators quickly detect and prevent advanced cyber threats and vulnerabilities in real time, ensuring total protection. Some of the future remote desktop security trends that could see tremendous growth in the upcoming time are as follows;
AI and ML integration
According to a recent study about AI in the workplace conducted by Goodfirms, 63% of professionals currently use AI for bug fixing, debugging, and identifying security flaws. AI and ML can analyze a huge amount of data in real-time, which is beneficial in quickly detecting and responding to cyber anomalies. They can learn from past data to find potential threats, proactively prioritize responses, quickly isolate the compromised endpoint, etc., minimizing the damage. Not only this, but AI and ML are also helping future remote desktop systems predictively allocate resources, automatically adjust bandwidth, improve remote connection experience, enhance remote desktop usability, strengthen compliance and auditing, etc. Additionally, with the ongoing evolution, the integration of AI and ML in remote desktop security will only help ensure better security, efficiency, and performance of remote desktop tools.
Zero-trust security models
Based on the “never trust, always verify” principle, zero-trust security models are among the most trending cybersecurity measures that are deployed by businesses. In this dynamic approach, businesses collectively use advanced access control features, latest cutting-edge technologies, and best practices to ensure security breaches are eliminated before they arise. Ongoing developments in zero-trust architecture including remote browser isolation, enhanced identity and access management, least privilege access, microsegmentation of networks, etc., will further help IT specialists in ensuring optimal security 24*7 in the future days to come.
Advanced endpoint protection and response
“To offer secure, efficient, and user-friendly IT experiences in the future, companies will need an always-on endpoint management infrastructure that can support this new way of working.” - Dr. Ian Pratt, Global Head of Security for Personal Systems at HP Inc.
In most of the cases, devices owned by employees, whether personal laptops or company-provided devices, are the likely origin point for cyberattacks. Additionally, employees are also more likely to use the professional work devices for personal work, thus increasing the attack surface. Only advanced endpoint protection and response systems equipped with AI, robust automation, and optimization measures can adapt the mechanisms to evolving threats. EDR systems can consistently monitor the endpoints behavior in real time that help them isolate infected endpoints and roll back changes to a stable point, ensuring minimal damage from the malware.
Conclusion
Here, we are in an era, where remote desktop security is paramount to the success of any business. Undoubtedly, modern remote desktop solutions are a reliable option to safeguard business data and IT infrastructure while connected to remote systems. In the last few years, numerous cybersecurity advancements have been made in the remote desktop software solutions, bringing better security, efficiency, and performance. From automating the vulnerability identification to the development of reliable security policies and protocols, present remote desktop software offers a robust set of features through which businesses can perform their remote functions without involving any risk of data threats and cyberattacks. Additionally, integration of technologies like AI & ML, developments in Zero trust security models, and advancements in endpoint protection and response have further capabilities to amplify the role of security measures in strictly preventing unauthorized access to the business systems. These breakthroughs are much more than technical upgrades but major shifts in prioritizing remote desktop security over convenience. However, no security system is full proof, therefore, it is critical for each and every business to employ a proactive approach with latest security measures, policies, and technologies to ensure optimal security of the entire IT infrastructure.




.jpg)



